
Prevent fraud with the next-gen identity signal
-
 95%global verification coverage
95%global verification coverage -
 85%decrease in promotion abuse
85%decrease in promotion abuse -
 6Xaverage return on investment
6Xaverage return on investment
Trusted by
-
 Marketplace appEngineering Lead, Trust & Safety and Verification(5 out of 5)
Marketplace appEngineering Lead, Trust & Safety and Verification(5 out of 5)"Incognia's geolocation product is excellent and has become an essential element of our Trust & Safety strategy. [It] allows us to ensure that our users are real people…[helping] us build a trusted, in-product community that has a much lower incidence of bad actors."
-
 Delivery appTech lead(5 out of 5)
Delivery appTech lead(5 out of 5)"Incognia has replaced our internal device id with a hyper-robust and reinstall-proof one. Their device intelligence technology has given us a new layer of emulator detection and, along with Incognia's device id, has significantly impacted chargeback and cancellation fraud reduction.”
-
 Delivery appSenior Product Manager(5 out of 5)
Delivery appSenior Product Manager(5 out of 5)"With Incognia, we've changed our fraud (Chargeback and Promo Abuse) scenario. Incognia helped us to improve our solutions to identify bad actors' in-app journeys.”
How does Incognia work?
The signal that stops fraud without friction
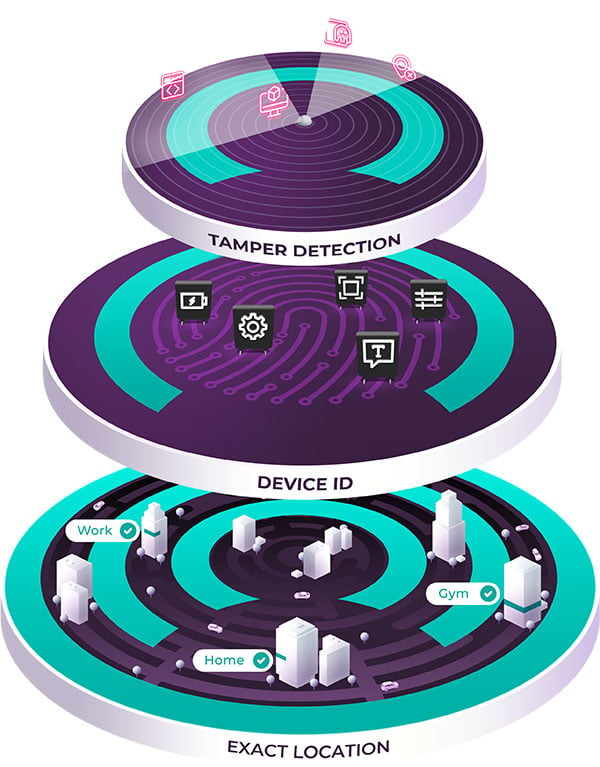
Tamper Detection
Location spoofing, root/jailbreak, app tampering & emulator
Device Intelligence
Device + location fingerprint Device ID
Indoor Location
Exact indoor location behavior, trusted & suspicious location recognition



