All you need to know about location technology [The Ultimate Guide]
Location is a word, from Latin locationem (nominative locatio) which means a particular place or position. When location is combined with the word technology it is understood to mean the use of sensors and methods for detection and calculation of the geographic location of either a mobile device, a person or thing, as part of the internet of things (IoT). Location technology is also sometimes referred to as geolocation technology.
The Global Positioning System (GPS) is the most well-known location technology, but there are also Enhanced Observed Time Difference (E-OTD) and Enhanced GPS (E-GPS) and now Wi-Fi and Bluetooth technologies can be used for the purpose of identifying a particular geographic position, particularly indoors.
Understanding mobile device location sensors
This is the era of mobile technology. Smartphones today are powerful computing devices with a number of sensors that provide real-time geolocation data to enable enhanced location-enabled information, entertainment, advertising, and most importantly, security services.
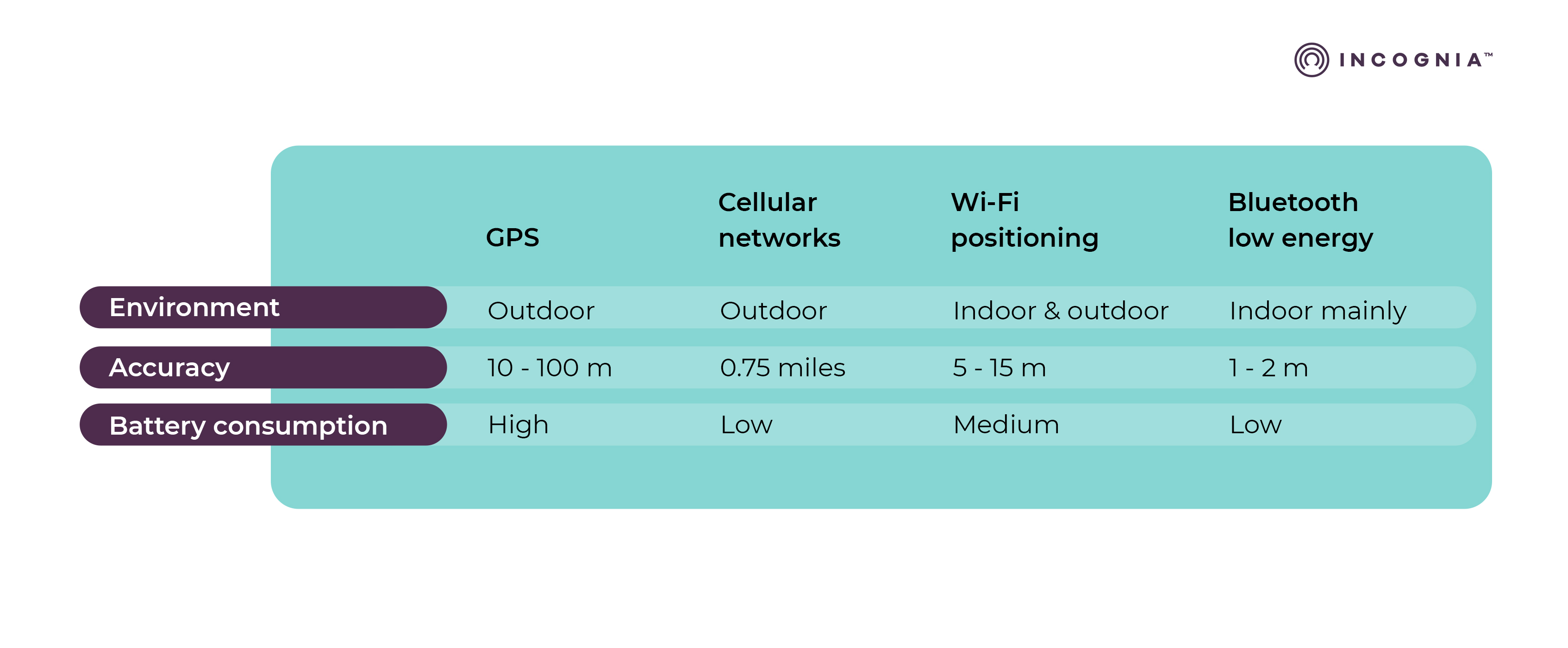
Global Positioning System (GPS)
GPS is the most widely used form of geolocation technology used on mobile devices and is also now regularly spoofed. GPS geolocation is based on communication satellites that orbit the earth, that continuously broadcast their status, exact location, and precise time. A GPS device that receives these signals is able to determine its GPS location. The accuracy of the GPS location is based on several factors including atmospheric conditions, signal blockage, and receiver design and quality, and it is between 33 to 330 feet. There are multiple techniques that fraudsters routinely use to spoof location, including GPS spoofing apps, VPNs, Proxies, and emulators.
Wi-Fi location positioning
Wi-Fi positioning, known as WPS or WiPS, is based on Wi-FI hotspots and wireless access points. The most common method for geolocation is based on measuring the receiving signal strength - known as the Received Signal Strength Indicator (RSSI) from a number of Wi-Fi hotspots or access points. Wi-Fi positioning is particularly useful for indoor positioning where GPS does not perform well.
Cellular location positioning
Cellular networks are enabled by a network of cell towers that transmit the radio waves that are used for mobile communication. Similar to how satellite signal broadcasts are used to locate a device, cell tower signals can also be used for geolocation, although this method is not as accurate as GPS, typically only accurate to within an area of 0.75 miles.
Bluetooth location positioning
Bluetooth is a wireless technology used for communicating short distances over short-wavelength radio waves between devices, with an accuracy between 1 and 2 meters. The most recent version called Bluetooth Low Energy (BLE) is built into many smartphones. Smartphones can determine their location based on picking up signals from BLE beacons enabling an indoor positioning system.
Besides the on-device sensors, other technologies can be used to access user’s location:
RFID
RFID monitoring is effectively a combination of methods. The RFID scanner typically has a static location. When it pings off of other networks, the location of the scanner can be logged. When the RFID scanner is activated, it can tag its location when it records the access. This can identify the location of the device accessing the scanner.
Fixed-location BLE beacons (Geobeacons)
Geobeacons are an example of in loco geolocation technologies, which are fixed-location BLE beacons. Their use is through BLE signals sent to monitoring devices to share their identifiers, enabling them to determine their position using low power.
What is the difference between location technology and location-enabled services?
Location-enabled services make use of a smartphone's GPS technology and other signals to track a person's location if that person has opted in to allow it. After a smartphone user opts-in, the service can identify their location without the need for manual data entry and, depending on the service, without personally identifying the user.
Location-based services depend on real-time location monitoring to deliver the services, meaning that the technology is persistently identifying the user's physical and geographical location to perform services and functions. The technology is most frequently used with mobile devices, but it can be applied to any device that is able to provide a location, including desktop PCs, based on considering multiple signals, including:
-
GPS
-
Nearby wireless access points
-
IP addresses
-
Cellular towers
-
MAC (media access control) addresses
-
Wireless routers
What is a location-aware application?
A location-aware application is an app that uses the location provided by the user, with their consent, after they opted-in, to deliver a service, information, or perform a specific task. The user location can vary from very precise to approximate. Also, the application needs to be explicit on why the user's location is necessary and how it is going to be used before the operating system allows it to run.
What is the main purpose of location-based applications?
Location-based apps are now part of our daily life and are often used. In case you are wondering what the main purposes of those apps are, they provide enhanced information, entertainment, advertising/personalized experiences, and most importantly, security services based on the users’ location. Core use cases include:
- Live Traffic, navigation, and public transportation apps
- Travel and check-in apps for travelers
- Social and dating apps
- Food delivery and restaurants
Is there a way to fool location technology? What is location spoofing?
As technology evolves, so do techniques used to fool security systems and fake location. GPS Spoofing, use of VPNs and Proxies, use of emulators, instrumentation tools, and app tampering are used by fraudsters to fake their location.
Location spoofing is used for many reasons. The first one is to evade geo-blocking. Geo-blocking is the act of restricting access to websites, systems, or other types of content available on the internet due to the location of the user accessing it, often resulting from regulation standards. Usually, geo-blocking applies to services such as streaming, gambling, gaming, and others.
Despite geo-blocking, criminals can use GPS spoofing to hide a person’s location. They may use a fake GPS location to make it seem like a person or object. These crimes can range from stealing rental cars to even kidnapping someone.
A spoofed GPS location can also pose cybersecurity risks. If hackers gain access to a cell phone, computer, or system, they can feed it fake location information to bypass certain security features and commit certain types of fraud that are commonly on the news, such as account takeover or SIM swap attacks. GPS spoofing technology can easily evade fraud detection systems that rely solely on GPS or IP addresses. Businesses that do not count on more robust technology, are very exposed to this type of threat.
How is location technology optimized?
It is key to analyze the context around location technology. For what purposes will you or your business use location technology? Is high accuracy and precision required? Is it going to be used solely outdoors or also indoors? Therefore, to extract maximum value from location technology, these questions need to be answered. Keep in mind that local regulations and availability need to be taken into account. It is worth building a matrix that compares the costs of each method - either implementation, consumption, and maintenance -, the accuracy required, the period of usage, and, finally but most importantly, the value added to business or to daily life.
Location technology for fraud prevention on mobile
Of all the recognition signals, location is the most relevant for fraud prevention on mobile. In today’s world, mobile devices have become an extension of ourselves. We carry our phones with us everywhere, and every person’s movements in the world are unique and create unique location behavior patterns. Mobile devices today contain many sensors that relate to motion and position and also the status of the device.
Using a location behavior signal as part of risk-based authentication on mobile offers the opportunity to provide an initial low-friction authentication option to legitimate users and only invoke higher security, higher friction, and authentication methods for high-risk logins or sensitive transactions.
Location permissions on mobile devices
iOS and Android mobile devices provide a number of user controls for setting permission related to the use of network signals, motion sensors, and the collection of location information. Understanding how these controls relate to location-enabled apps will help you to choose which are the best ones for your needs. Below are the types of location permission on iOS and Android devices.
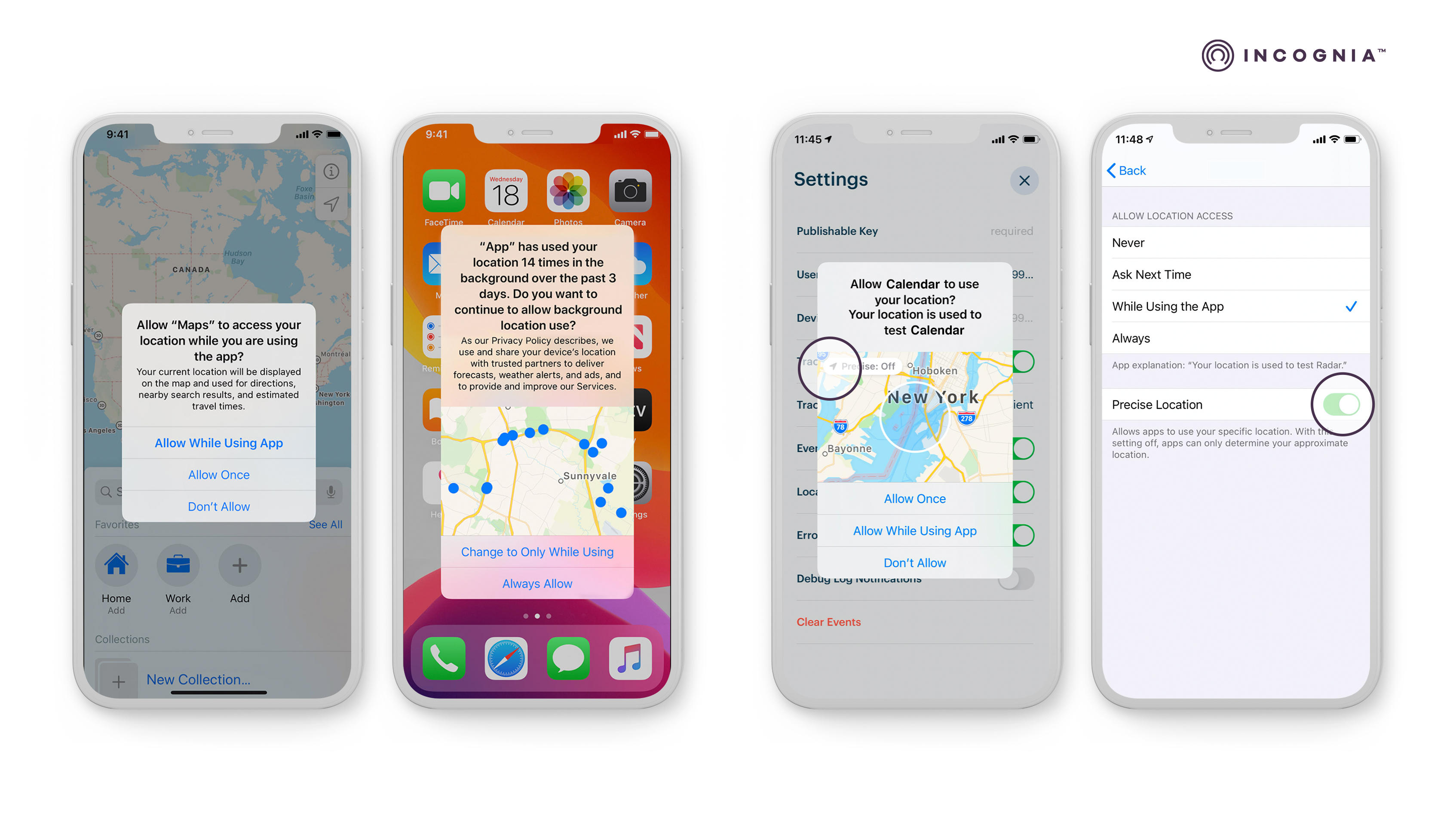
iOS - Location permissions
The iOS system includes several important features that relate to location permissions User Control of Location Sharing For iOS devices using iOS 14 or later, Apple users may choose between four options when deciding to share their location data with an app. However, before users decide to share their location with an app, it is required for the user to enable Location Services. This feature allows Apple and third-party apps and websites to use user location data to offer different location-based services.
Be aware that by enabling location services, the user will allow different features related to the location to be enabled, such as routing and traffic or location-based alerts. And to use those services, it is necessary that the user provides location permissions to each app before the app can start using user location data, choosing between the following:
- Don’t allow: prevents access to Location Services information.
- Allow while Using the App: allows access to Location Services only when the app or one of its features is visible on screen. If an app is set to While Using the App, the user might see the status bar turn blue with a message that an app is actively using location.
- Allow Once: this allows the app to access the user’s location during that one interaction.
- Always: this option allows access to location even when the app is in the background. It is only shown after the user selects “allows while using the app”. If the user has given this type of permission for previous versions of the OS, the new version will provide a new pop-up, so the user can confirm if “always” will continue to be the chosen option.
- Precise and approximate location: a user can choose between providing an app's precise location or an approximate location. According to Apple, precise location is “information that describes the location of a user or device with the same or greater resolution as a latitude and longitude with three or more decimal places”, while approximate location is “Information that describes the location of a user or device with lower resolution than a latitude and longitude with three or more decimal places, such as Approximate Location Services”. For Incognia, the use of precise location will provide higher accuracy in location detection.
- App monitoring transparency: Beginning with iOS 14, Apple introduced the AppTrackingTransparency framework to manage the app monitoring authorization request and status for any app that collects data about end-users and shares it with other companies. So, if your app shares data with Incognia, it is recommended to request the user’s authorization using the AppTrackingTransparency framework available on iOS 14. The iOS 15, delivers a new privacy dashboard. In this dashboard, the user can check which apps are accessing their location - after the user gives their location permission - and how often it occurs.
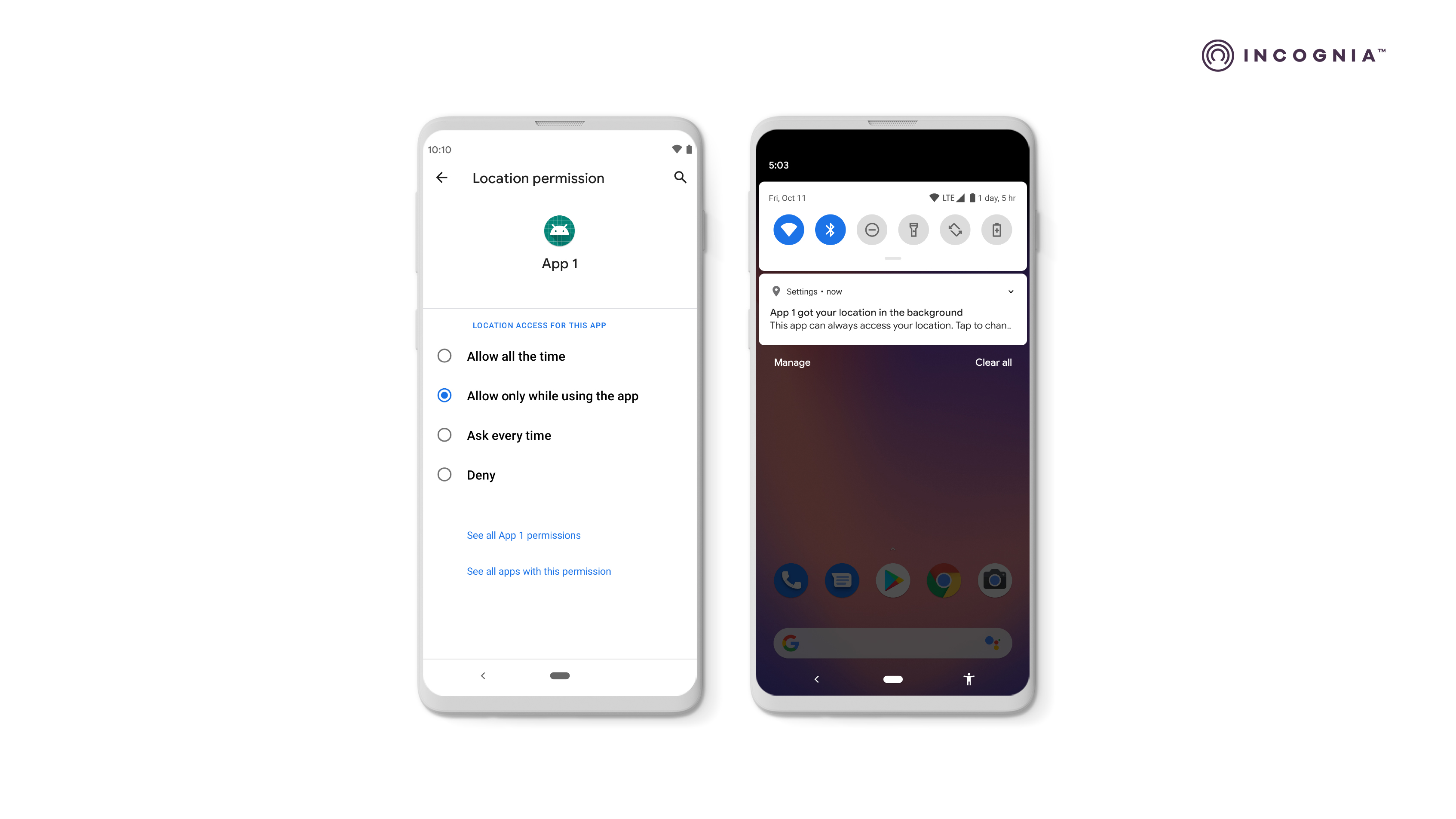
Android - Location permissions
The Android system has two different types of location permission: foreground and background location permission.
Foreground location: If an app has a feature that shares or receives location information only once, or for a defined amount of time, then that feature requires foreground location access, which means that location permission is given while the user is using the app, or only that defined time or even the option of denial. And, the newest Android version, yet to be released, will also have the possibility to choose between fine or coarse location, as currently supported in ioS.
According to Android developers, removing location or changing it from background to foreground location can help apps be battery-efficient and avoid poor app ratings when users don’t want to share their location. So, apps are always challenged to prove why they need user location.
Background permission: Asking for background location permission can apply to apps that have a feature that constantly shares location in different situations, such as sharing with other users or when Geofencing is on. On Android 11, users must enable background location on a settings page, as shown. Android has a background access location reminder, which makes the user aware of the apps accessing their location and makes it easier for the user to decide if they want to keep those permissions on or maybe turn them off.
Android provides an example of clear messaging that shows the benefits of accepting location permissions. Due to its size, this messaging could be added to privacy policies as the complete version and or reduced to fit the location permission request.
Is there a way for users to opt-out of location?
Based on privacy regulations, including GDPR, at Incognia we believe that the user should have control of their data and be given the choice of whether to share their location with apps or not, following the guidelines provided by the operating systems. It is important to reinforce that location permissions can help provide a more secure in-app experience, helping to identify cases of identity theft, GPS spoofing, and other fraudulent techniques currently being used.
How do we know which apps are using location?
- Android Go to settings > Apps > Apps permissions > Location
- iPhone Go to settings > Privacy > Location services
Consent to collect location data
Under GDPR - fraud prevention is considered a legitimate interest to collect data. ICO says that “the UK GDPR highlights certain purposes that either ‘constitute’ a legitimate interest or ‘should be regarded as’ a legitimate interest.” These are:
- Fraud prevention;
- Network and information security; and
- Indicating possible criminal acts or threats to public security.
As a further illustration, it is a legitimate interest of mobile retailers and financial services to use mechanisms to assist in user identification, fraud prevention, and financial crimes. The user has the legitimate expectation that apps will have fraud prevention solutions for validating their registration, preventing theft of their credentials, and identifying fraudulent transactions. When location is used to increase security and prevent fraud, an important question is often asked: “But why would a fraudster, in this case, share their location?” That is one of the reasons why data protection laws, such as LGPD and GDPR emphasize that, when preventing fraud, explicit consent is not necessary, as it is the legitimate interest of the user to remain secure.
Note that although explicit consent is not required, the obligations of transparency and the rights of the data subjects must be observed. So any app should provide information in your privacy policy about the processing of device data by third parties for fraud prevention.