What is Adaptive Authentication and its advantages?
What Is Adaptive Authentication?
Adaptive authentication is the process of authenticating a user based on the risk level presented by a login attempt. An essential component of it is the use of multi-factor authentication. Typically the risk level is assessed automatically by the first authentication method, and if the fraud risk is low, the login is granted. If the risk is high, step-up authentication is triggered and the user is asked for another type of authentication. Ideally, the first authentication method used in this approach should present the lowest friction for users. In this way, the majority of users, who are legitimate, will be able to log in easily. Higher friction authentication methods will be used as additional steps for the users that were flagged as high-risk in the initial login attempt. Since risk is the defining factor to determine the ease for the user to log in, adaptive authentication is also referred to as risk-based authentication or context-based authentication.
Adaptive authentication offers the opportunity to lower friction for trusted users logging into their accounts and systems from trusted locations that represent a low risk. For higher-risk logins, adaptive authentication can request additional authentication credentials. This way, trusted users don’t have to waste their time verifying their identity every time they access a system with additional Multi-Factor Authentication (MFA).
This access management approach is superior to simply granting user access after only presenting a username and password, since, not only it can improve user experience, requiring the user to do less effort on their end, but it also can improve security due to the intrinsic weakness of passwords, which could be ditched from the authentication process.
Methods to deploy Adaptive Authentication
There are several methods to implement adaptive authentication. Usually, the first authentication method, which could authenticate the user continuously, has to identify if there is an anomaly in the user login credentials or behavior. An anomaly could be an incorrect password or different location, device, or behavior from what is usual for the user in question.
[banner_1]
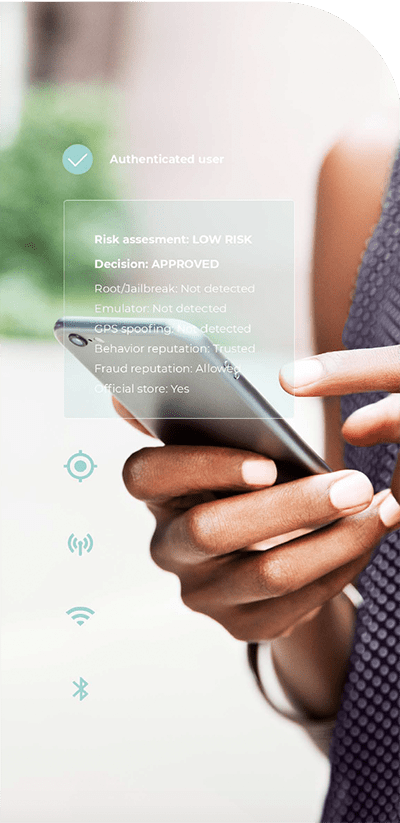
Today location is most often determined by either the IP address or GPS but increasingly location behavior based on a combination of WiFi, Cellular and GPS signals is being used to identify location behavior patterns with a high degree of accuracy in both outdoor and indoor. If the location of the user trying to login does not match other previously identified locations, where the user usually is when in other login sessions, then step-up authentication, such as an authenticator app or face recognition would be required. The main differences between the location technology methods are the level of precision and accuracy and also resistance to spoofing. IP address and GPS can easily be faked or spoofed, while a more sophisticated location behavior technology cannot be spoofed.
Another possible scenario is when a new device is detected at login. It could either be the user actually trying to change their device, or a fraudster trying to log in with stolen credentials from a new device. In this case, step-up MFA could make use of a recognition signal, such as location behavior to assess the risk associated with the login. If the user is not only using another device but is also at a completely different location that does not match with the user’s usual location behavior pattern, this can be flagged as high risk. In this case, a second authentication method could be triggered, such as a mobile push notification or requesting the use of an authenticator app, or anything that verifies the previously used device as a token of the user's possession.
These are only two among many possible examples of combinations of authentication methods to deliver adaptive authentication using both multi-factor and step-up authentication.
For further information on when each type of authentication would be used please read step-up authentication vs. multi-factor authentication.
How Does Adaptive Authentication Work?
The first thing that should be done when determining risk-based authentication solutions is to define the parameters that users will be held to when logging into the system. As users attempt to gain access to systems, they will be assigned a risk factor score. These scores are important because, depending on what they are: low, medium, or high, the user will need to provide more information before the system can authenticate their identity.
Authentication and authorization are two main steps in the security of a system. The risk score is part of the authentication part of the process. In any risk-based authentication solution, if the first method of authentication does not identify the user, automatically that login presents a higher risk. Additional authentication methods can provide a risk score, ranging from low to high.
One or more of the following MFA methods may be triggered based in the case of high-risk score of an authentication request:
Face Recognition: The user may be required to take a selfie with liveness detection to prove their identity.
OTP over Email: The user receives a notification regarding the login attempt via email and is requested to enter the one-time password sent via email.
Push Authentication: The system authorizes access by delivering a push notification on the user’s trusted device and requesting the user to acknowledge the notification.
OTP over SMS: An SMS notification about the authentication request is sent on the user’s device. The user is requested to enter the one-time password sent via SMS. Although this method does not provide high security, it is still widely used.
The authorization then would come into play to provide usually three outcomes to that authentication attempt:
- Allowed access
- Denied access
Adaptive Multi-factor Authentication
Adaptive multi-factor authentication lets organizations deploy the appropriate authentication factors based on the consumer’s behavior and risk profile. The Identity Service Provider system selects authentication tools after evaluating the risk of the user’s profile and behavior and adapts the authentication requirements according to the situation.
Adaptive authentication can be used either as a complement or alternative to multi-factor authentication. An adaptive MFA can help reduce the burden on users by requiring multi-factor authentication only when an access request seems malicious or high risk. Adaptive MFA solutions can increase or decrease authentication methods based on contextual factors such as:
- Device profile including the recognition of system and device used for logins
- User behavior and user role analysis
- Location intelligence, including trusted locations, places the user frequently visits, geo-velocity, which is the physical distance between consecutive access requests
- Source IP address and operating system information
- Third-party threat intelligence data
Using these context-based authentication factors, the organization can pair risk levels with suitable authentication requirements, such as prompting for MFA, allowing or blocking access to the system or using passwordless authentication for low-risk situations. These authentication tools help organizations differentiate between fraudulent users and authorized users.
Unlike one-size-fits-all authentication procedures, adaptive MFA creates suitable access requirements according to the varying risk level of different situations. This way, context-based authentication minimizes unnecessary authorization requirements and provides a better user experience with enhanced security during risky situations.
Benefits of Adaptive Risk-Based Authentication Solutions
When it comes to adaptive risk-based authentication, there are several benefits for companies and users.
Adaptive or risk-based authentication prevents low-risk activities from being burdensome and high-risk activities from being easy to hack. Context-based authentication analyses user behavior to configure appropriate security levels. Here’s how adaptive authentication benefits organizations:
- It provides frictionless authentication for the users by reducing needless heavy-handed levels of authentication while protecting the system against fraudulent access requests.
- It offers a comprehensive and updated security layer by analyzing the risk factors and consumer behavior.
- It provides flexible and secure access to customers, partners, and employees regardless of their location.
- Risk-based authentication triggers only elevated-risk situations and helps avoid unnecessary long authentication processes.
- It creates low entry barriers and fewer interruptions for users accessing non-sensitive information and high-security adaptive multi-factor authentication for users requesting access to sensitive gateways.
- It offers easier deployment and maintenance for IT staff by limiting identity challenges.
- Context-based authentication solves the BYOD (bring your own device) security headaches by differentiating between mobile devices and their different security vulnerabilities.
With the looming fear of fraud taking place, a company might face the temptation to force users to jump through more authentication hoops. This can lead to frustration and users abandoning their session before they've completed their transaction in the system.
With the technology available today, users can face a lot less friction or even zero-friction on their login. By adapting the authentication method based on the risk level, lower risk methods can be used initially, saving the highest friction authentication methods for the higher risk logins. Recognition signals from sensors on the device can provide insights on mobile user behavior and device intelligence without requiring any action by the user. Working in the background these types of recognition signals enable a seamless experience for the user, where they might not even realize they are being continuously authenticated. Zero-friction also can be accompanied by high security, since there are many methods that could recognize such users, with mobile recognition signals being only one of the possible examples.
Risk-based authentication can provide lower false-positive rates for companies, which can result in higher revenue since more users are provided with a better experience and complete more transactions. Also, an adaptive authentication approach can result in a higher quality of defense against fraudsters.
Implement Adaptive Multi-factor Authentication for Your Organization Today
Companies need to tighten their security to keep fraudsters and hackers out of their systems. Adaptive authentication is a powerful approach that offers higher-level security by limiting the ability of unauthorized users to use any compromised credentials to steal valuable financial data and funds, intellectual property, and other sensitive information.
Adaptive authentication solutions can be customized according to the company’s risk tolerance, allowing the balance of better user experience and security. Incognia authentication solutions can help organizations recognize the level of risk and handle authentication requests based on location behavior and device sensor signals. Get in touch to learn more about Incognia’s adaptive authentication solutions.