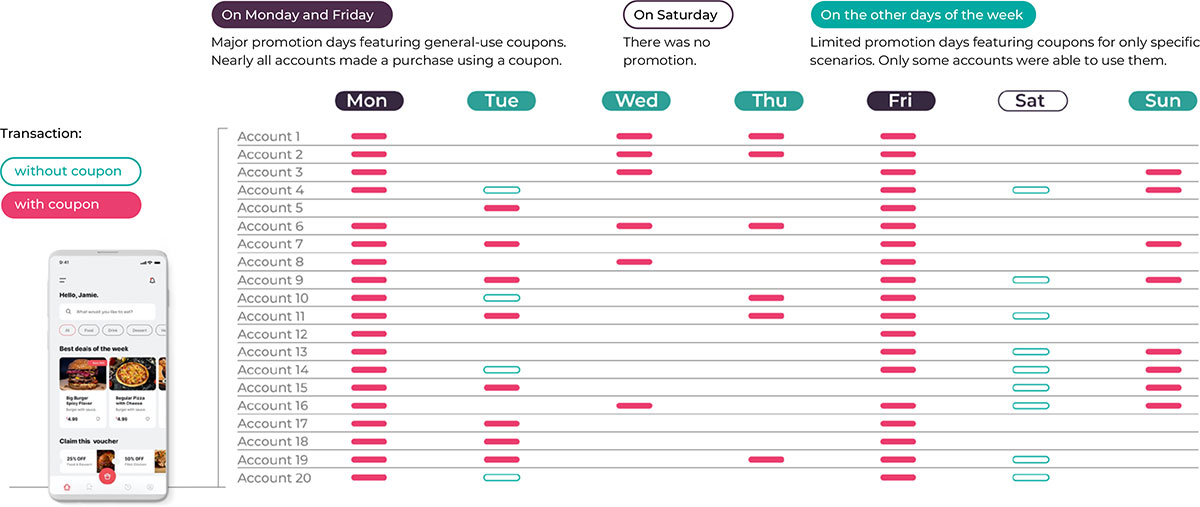
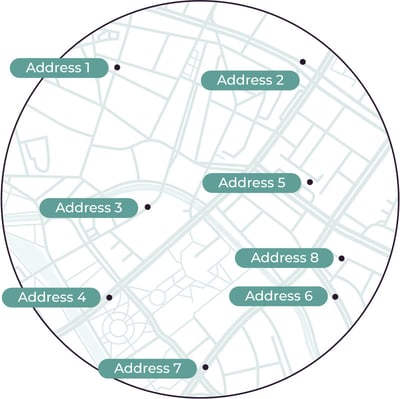
The food delivery industry experienced major growth during the COVID-19 pandemic. These marketplaces saw the demand for their services grow, but also experienced intense competition.
Post-pandemic, user growth slowed, and food delivery companies had to implement new customer acquisition and retention strategies. In the face of this new environment, food delivery companies have invested—and continue to invest—substantial sums in promotional activities.
For example, in Latin America (LATAM) today, Incognia estimates that between 20-40% of monthly transactions on food delivery platforms use some form of promotional coupon.
Some of these transactions are performed by legitimate customers just looking for a good deal. But many of them are made by bad actors who are systematically abusing promotional activities and stealing large sums of money from these platforms using sophisticated fraud methods.
How extensive is this problem of promotion abuse? By our estimates, on average 2% of all monthly transactions on delivery platforms in LATAM are associated with coupon fraud. With the top two US delivery platforms averaging US $1.1B worth of transactions per month, we estimate that the largest US delivery companies each could be losing over US $1.5M per month due to promotion abuse.
To systematically abuse coupons, bad actors typically use a multi-accounting strategy in which they use several devices and utilize a sophisticated device reset strategy to evade recognition. As they’ve implemented limits and rules in an attempt to crack down on this behavior, fraudsters have come up with increasingly complex techniques to get around the restrictions so they can continue to profit. Given the strategic combination of these multi-accounting techniques and their lack of advanced location and device recognition signals, the delivery industry has been fighting blind.
The Incognia team has extensive experience fighting promotion abuse through close collaboration with our customers.
We’ve compiled this report to provide food delivery companies around the world with deep insights into two kinds of promotions that are commonly abused: New User Coupons and Loyalty Coupons.
To illustrate the scope and complexity of these issues, we’ve included real insights from the food delivery market in LATAM. Our goal with this report is to help fraud practitioners gain a deep understanding of the true sophistication and scale of promotion abuse on food delivery platforms, and the tools, techniques, and new signals that can be used to prevent it.