As gig platforms mature, the tactics used to exploit them are evolving just as quickly. Fraud in 2025 is driven by a mix of familiar abuse types—collusion, refund scams, promo abuse, chargebacks—but the mechanics behind them are shifting.
Multi-accounting and ban evasion remain key enablers of fraud at scale, allowing bad actors to return again and again under new identities. At the same time, device manipulation tactics like app cloning and code injection are quietly undermining the core signals that teams rely on to assess risk, yet fewer than half of surveyed respondents say their platform leverages tamper detection.
An important change is how accessible sophisticated fraud tactics have become. Fraud-as-a-Service (FaaS) offerings and automation tools are lowering the barrier to entry, making it easier for less experienced actors to scale their efforts. Collusion remains one of the hardest types of abuse to detect, especially when platforms manage different user types in separate systems and lack shared risk signals.
Without stronger foundations—protection against multi-accounting, tamper-resistant signals, cross-role visibility, and defenses built for scale—platforms risk falling behind as fraud accelerates.
Executive summary
Introduction
To better understand how platforms are responding to the current fraud landscape, Incognia surveyed fraud & risk professionals from delivery and ride sharing platforms. This report combines their responses with our expert analysis to highlight key trends, emerging risks, and the areas where platforms may need to reinforce defenses before abuse scales further.
Survey respondents at a glance
We surveyed 42 professionals working in fraud, product, operations, and data science across a wide range of company sizes, from early-stage startups to global platforms with dedicated fraud teams of over 100 people.
Respondents also represented different sides of the marketplace: driver and courier, rider and diner, or both—providing a clearer picture of how fraud affects multiple sides of the platform.
Together, these perspectives provide a well-rounded view of how teams across the ecosystem are tackling fraud in 2025 and beyond.




Fraud and abuse concerns
2025

Today’s leading fraud and abuse concerns are:
- Collusion – 24%
- Chargebacks & payment fraud – 24%
- Refund abuse – 19%
- Promo & referral abuse – 14%
- Account sharing & renting – 14%
- Cancellation abuse – 14%
Some of these concerns—like chargebacks, refunds, and promo abuse—are familiar platform challenges that aren’t surprising to see near the top of the list. But what is surprising is that collusion is tied for the top spot. We go deeper on this later in the report.
One clear pattern emerges: multi-accounting and ban evasion are a key part of the engine behind many of these concerns. Abuse at scale—whether it’s stacking promos, exploiting refunds, or coordinating scams—typically depends on the ability to create and recycle accounts without getting caught. And collusion and cancellation abuse can rely on the same cycle.
It may be tempting to focus on the downstream symptoms of fraud because they show up clearly in losses and metrics. But the root causes often sit upstream. If platforms can close the gaps that enable account recycling, they can weaken multiple fraud vectors at once.
2026

Looking ahead, respondents report a shift in priorities. The top concerns for 2026:
- Collusion – 24%
- Chargebacks – 17%
- Promo & referral abuse – 17%
- Ban evasion – 14%
- Driver compensation – 14%

Collusion: Hard to detect, hard to measure
One of the more surprising findings is that collusion is a consistent top concern in both 2025 and 2026.
Collusion can take many forms. It might involve multiple people—like a courier and a restaurant—collaborating to share insider knowledge of platform policies and design more sophisticated schemes. Or it might be a single actor using multiple accounts or devices across roles to defraud the system. Either way, it’s a uniquely challenging problem for gig economy platforms, where activity spans multiple user types and app interfaces—courier, consumer, restaurant, and more.
Unlike chargebacks or refunds, which can be tracked with clear metrics, collusion crosses technical and organizational boundaries. Some platforms manage these user types in separate systems, making it hard to connect signals in real time. As a result, teams may end up having to piece evidence together after the fact to identify collusion—shared delivery addresses, repeat order patterns, or suspicious handoff flows.
The fact that collusion is a top concern now and for 2026 may point to how fragmented some platforms’ systems still are. Without consistent risk signals across user types, collusion can slip through the cracks. A courier and customer account may look unrelated—unless solutions like cross-platform device ID and precise location intelligence are in place to detect that they are accessed from the same device.
Manipulation concerns
2025

On the manipulation side, respondents ranked these tactics as their biggest challenges currently:
- App cloning – 29%
- App tampering / code injection – 26%
- Device farms – 21%
- Device rooting / jailbreaking – 19%
These techniques are often combined to power abuse. App cloning allows fraudsters to manage dozens of accounts on one device. Tampering and code injection disguise devices and bypass weak device identifiers. Device farms can spread these behaviors across dozens or hundreds of devices, while rooted or jailbroken phones create the permissive environments that enable tampering in the first place.
The common thread is that these tools are increasingly easy to leverage—especially with Fraud-as-a-Service vendors lowering the barrier to entry—yet remain difficult to defend against. What once required custom setups and technical know-how is now often available off the shelf, making industrial-scale abuse accessible to far more actors.
2026

By 2026, manipulation concerns shift slightly:
- App tampering / code injection – 29%
- Bots and script automation – 24%
- Device farms – 21%
- App cloning – 19%

In 2026, tampering becomes the leading concern, while bots and automation are on the rise. Our respondents appear to be bracing for more scripted operations to industrialize account creation, credential testing, or repetitive abuse flows.
Device farms remain a steady enabler—and based on what the Incognia team is observing, these operations are not just growing in number but increasingly appearing using iOS devices. That’s a notable shift, given iOS has traditionally been seen as a harder environment to manipulate. Overall, this trend suggests that our respondents expect device farms will continue to play a central role in powering fraud at scale.
Fraud prevention tech stacks
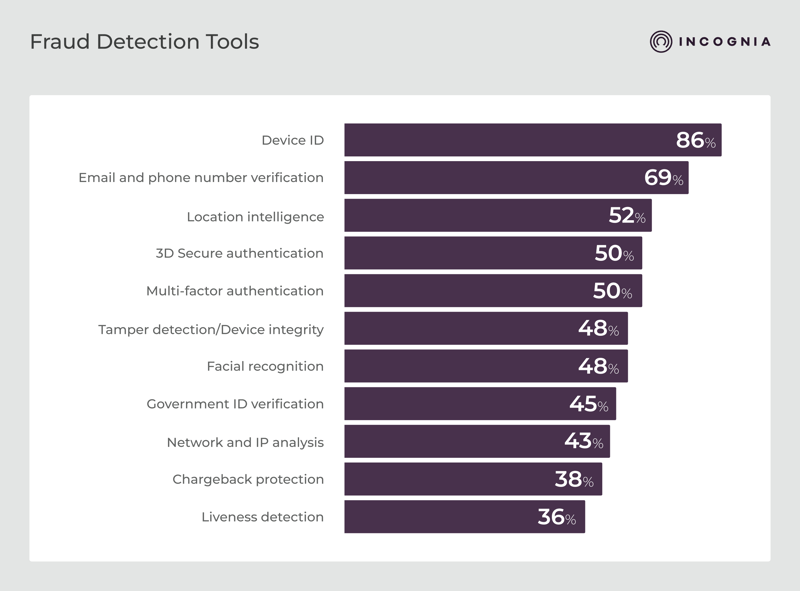
Respondents reported these as the most widely used fraud prevention tools on their platforms:
- Device ID — 86%
- Email & phone verification — 69%
- Location intelligence — 52%
- 3D Secure — 50%
- MFA — 50%
- Tamper detection — 48%
- Facial recognition — 48%
It’s interesting to see that usage of a device ID is nearly universal—yet fraud types like promo abuse and refund abuse still rank among the top concerns. These are exactly the kinds of issues a strong device ID should help address. That raises a key question: are some platforms using a version of device ID that isn’t strong or accurate enough to solve the problems they’re prioritizing?
The Incognia team often sees this in the field. Some platforms rely on easily bypassed identifiers, like advertising IDs. Others have built in-house tools that lack the sophistication to stop fraud at scale. In these cases, having a solution isn’t the same as having the right one—or using it effectively.
Tamper detection adds another critical layer. Despite its importance, fewer than half of respondents report using it. That’s a concern, because without tamper detection, even the best device ID, facial recognition, or location solution becomes unreliable. If a device has been tampered with—for example, through app cloning, code injection, or virtualization—the signals it sends can’t be trusted. Tamper detection isn’t just another control; it’s the foundation that gives other signals their integrity.
The same holds true for tools like location intelligence. When implemented well, it can help reduce behaviors like account sharing, collusion, or compensation abuse. But as with device ID, impact depends entirely on the strength of the solution.
Ultimately, it’s not about simply having a tool in place. What matters is whether the solution is the right kind for the use case, applied consistently across areas of the business, and strong enough to solve the problems it’s meant to address.
Fraud tool budgets

Most survey respondents report stable or increasing spending for fraud prevention tools, and very few expect cuts. It's good to see that investment in fraud prevention tooling isn’t being deprioritized. But does this mean fraud prevention is now receiving the appropriate level of resources across platforms? Not necessarily.
Fraud prevention has long been seen as under-resourced at many platforms, and rising tool spending may simply indicate teams are catching up to where they should be. Even with increases, current tool spend may still fall short of what’s needed to match the scale and sophistication of modern fraud.
That’s why advocacy remains critical. Fraud teams may struggle more than operations or growth teams to show direct cost savings or revenue impact, making budget advocacy a vital skill. For this reason, fraud leaders should constantly refine their ability to frame the impact of their team's work in business terms.
At the same time, some platforms may be shifting from the “growth at all costs” mentality that was more common in the early 2020s to a mindset of efficiency and profitability. In this environment, fraud prevention may attract more investment as loss prevention is increasingly recognized as directly impacting the bottom line.
The key takeaway: spending on fraud prevention tools isn't shrinking, which is positive. But for underfunded teams, securing more investment may depend on strengthening their ability to demonstrate business value—positioning fraud prevention not just as risk reduction, but as a driver of efficiency and profitability.
Looking ahead
Based on these findings, we see five areas where platforms can strengthen their approach to fraud prevention.
1. Tackle multi-accounting and ban evasion at the root
From promo abuse to refund abuse to collusion, most top fraud types share a common root—multi-accounting. Fraudsters exploit weak identity controls to create and recycle accounts endlessly, powering abuse at scale. To break this cycle, platforms should prioritize strong device-based identity and behavioral signals that make it much harder for banned users to sneak back in.
2. If you don’t trust the device, you can’t trust the signal
App tampering, code injection, and app cloning are top concerns, but fewer than half of platforms are using tamper detection. That’s a problem. Once a device is compromised, every downstream signal becomes suspect, from device ID to facial recognition. Tamper detection isn’t just another checkbox in the tech stack. It’s the bedrock that gives every other fraud signal its reliability.
3. Be prepared for industrialized fraud
Fraud-as-a-Service, device farms, and cloud-based tools are making sophisticated fraud techniques far more accessible. What used to require custom setups and technical expertise can now be rented off-the-shelf, lowering the barrier to entry for less experienced actors. FaaS is democratizing methods that were once reserved for a smaller number of advanced fraudsters, while AI tools are enabling them to scale their operations in ways they couldn’t before. Platforms need to be ready for this shift—because as advanced fraud gets easier to access, stronger defenses are the only way to keep it from scaling.
4. Break the silos to catch collusion
Collusion thrives when teams work in silos. To fight it, platforms need shared goals and KPIs, consistent risk signals across different user types, and the ability to run joint investigations. Using the same device ID solution across all user types allows platforms to spot when, for example, a courier account and a merchant account are operating on the same device—connections that can be missed when signals are fragmented.
5. Make the business case: Fraud prevention = profit protection
Stable or growing budgets don’t always mean fraud teams have what they need. Fraud prevention is still often under-resourced, partly because its impact is harder to measure than functions like growth or operations. That’s why fraud leaders must be more than experts—they need to be advocates. The key is storytelling: connect fraud metrics to business results. When you can successfully frame prevention as a driver of efficiency and profitability, it becomes much harder to ignore.
Final thoughts
Fraud on gig platforms isn’t new, but the scale and accessibility of today’s tactics are.
This year’s findings highlight a mix of persistent challenges and emerging risks—from multi-accounting and collusion to device manipulation and automation. While the concerns vary, many share the same root enablers: weak identity signals, siloed systems, and gaps in foundational defenses like tamper detection.
As abuse evolves, platforms that proactively close detection gaps, connect risk signals across user types, and strengthen core signals will be better positioned to keep fraud from scaling.
