- Blog
- A Comprehensive Analysis of Device Fingerprint Spoofing Techniques
A Comprehensive Analysis of Device Fingerprint Spoofing Techniques
Device fingerprinting has long been used to identify devices and detect fraud, but it’s becoming easier to evade as privacy controls tighten and spoofing techniques evolve. Fraudsters can reset devices, manipulate attributes, and disguise activity to avoid detection by legacy fingerprinting methods. Combining modern device intelligence with tamper-resistant signals like location intelligence creates a more persistent and reliable way to identify risky behavior without adding friction for legitimate users.
Subscribe to Incognia’s content
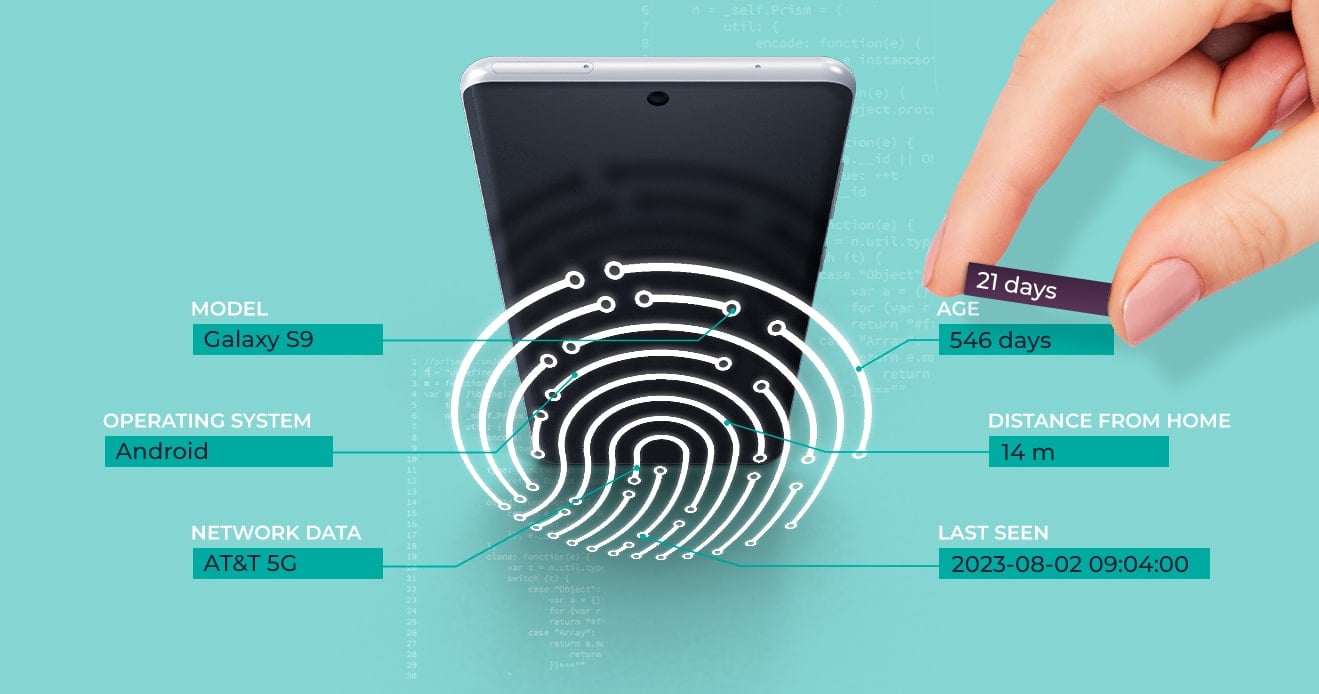
Device fingerprinting is the process of collecting unique information from a device to create a fingerprint you can use to uniquely identify that device—just like human fingerprints uniquely identify each of us. This information includes a device’s attributes, hardware, software, location, and behavior.
For years, device fingerprinting played an important role in identifying users and detecting fraud. But the environment it operates in has changed dramatically.
As device fingerprinting became more common, privacy-focused users—and fraudsters—started looking for ways around it. Today, there are many techniques designed specifically to disrupt device-based identification by manipulating or masking device data.
One of the most effective of these tactics is fingerprint spoofing.
If you think about it in real-world terms, fingerprint spoofing is like a criminal altering the ridges on their fingertips to avoid being linked to a crime scene.
That raises a critical question for fraud teams: How do you reliably identify users when the device data you’re collecting can no longer be trusted on its own?
To answer that, it helps to understand how spoofing actually works.
Key TakeAways
- Device intelligence can be a valuable tool in the fight against fraud, but fraudsters can easily spoof legacy device fingerprinting solutions
- Factory resets, third-party tools, and the manipulation of device attributes are just a few fingerprint spoofing methods
- Combining next-generation device intelligence with additional signals like location makes for a more persistent, tamper-resistant signal
Why traditional device fingerprinting is losing effectiveness
For several reasons, device fingerprinting alone is no longer as effective as it once was.
Platform providers like Apple and Google have made it significantly harder for developers to collect device attributes, largely in the name of user privacy. At the same time, the rapid emergence of new device models and operating systems has increased fragmentation across the ecosystem.
User behavior has changed as well. VPNs, incognito browsing, and privacy tools are now mainstream, making consistent device identification more difficult.
On top of all of this, fraudsters themselves have become far more sophisticated. Many now actively manipulate or mass-change device attributes at scale to evade detection and trick traditional fingerprinting systems.
The result is declining reliability. And that decline has real consequences: US consumer fraud losses grew 25% year over year from 2023 to 2024, exposing how vulnerable digital accounts have become as legacy signals weaken.
The history of device fingerprinting: then and now
Device fingerprinting dates back to the early days of the internet. In the 1990s and early 2000s, cookies were the primary way to track users online. By the mid-2000s, device fingerprinting began to emerge as a more advanced and reliable alternative.
The introduction of Flash and JavaScript enabled deeper data collection, improving accuracy. As browsers and devices evolved, so did the richness of available signals. In 2010, the Electronic Frontier Foundation’s Panopticlick study demonstrated just how effective browser fingerprinting could be.
With the rise of smartphones in the 2010s, device fingerprinting expanded beyond browsers to include various device-level data points. Today, with the rise of the Internet of Things (IoT), the technology continues to evolve, incorporating data from a plethora of interconnected devices.
But as the technology evolved, so did the countermeasures. Today, device fingerprinting—when used in isolation—no longer provides the durability it once did.
Common device fingerprint spoofing techniques
Device fingerprinting is still widely used, but it’s far from foolproof. Fraudsters now employ a mix of simple tactics and advanced tools to obscure or reset device identities.
1. Factory resets
This is by far the simplest method of evading device fingerprint.
By wiping a device and restoring it to default settings, fraudsters can continue abusing a platform even after the device has been flagged.
Traditional fingerprinting solutions typically can’t re-identify a device once it’s been reset. And since resets require no technical expertise, this method is easy to scale.
2. Third-party apps and plugins
Many third-party apps and browser plugins allow users to modify device and browser attributes, including timezone, fonts, screen resolution, and more.
While these tools are often marketed to privacy-conscious users, they’re equally useful for fraudsters trying to avoid detection.
3. Manipulating device attributes
More technical actors can manually alter attributes like IP address, operating system details, software versions, and device IDs.
Since fingerprinting relies on these signals, changing them periodically makes consistent identification much harder.
4. Presenting a false user agent (UA) string
User agent strings tell servers what type of device and browser a user is on, so the correct version of a site or app can be delivered. Without them, you might open a website on your desktop and end up seeing the mobile experience instead.
Because user agent strings include details about operating system, device type, and browser, they’re also commonly used in device fingerprinting. When fraudsters spoof these strings, they can provide false attribute data and make activity from a single device appear as though it’s coming from many different devices.
How to detect device fingerprint spoofing
Because of these techniques, device fingerprinting alone can’t be trusted.
A stronger approach combines modern device intelligence with an additional, tamper-resistant signal. Incognia does this by pairing device intelligence with location intelligence, not traditional device fingerprinting.
Consider a common scenario: a fraudster repeatedly factory-resets a device to abuse new-user promotions on a food delivery app.
If device fingerprinting were the only signal in play, the platform would see what looks like a stream of brand-new devices. The abuse might go undetected entirely.
Location intelligence changes that.
By analyzing GPS, WiFi, and Bluetooth signals, platforms gain a more persistent view of user behavior. Even if a device is reset or spoofed, consistent location patterns can reveal that the activity is coming from the same person using the same device.
In fact, combining these signals can create a location-based identifier with a false positive rate of less than 1%, making it highly reliable for re-identification.
Device integrity checks add another layer. By identifying rooted devices or known spoofing tools, platforms can flag risky behavior earlier in the user journey.
Beyond fingerprinting: modern device intelligence
Device fingerprinting has reached its limits. As fraudsters adapt and privacy controls tighten, relying on legacy approaches leaves platforms exposed.
Modern device intelligence, especially when combined with location intelligence, provides a more resilient, spoof-resistant signal. Together, they make it far harder for fraudsters to hide behind resets, spoofed attributes, or manipulated devices.
That’s how platforms protect revenue, reduce abuse, and keep experiences smooth for legitimate users.