- Blog
- Fraud farms - Identifying where fraudsters are
Fraud farms - Identifying where fraudsters are
Andre Ferraz of Incognia and Shawn Colpitts of Just Eat answer pressing fraud farm questions in podcast and webinar episode
Subscribe to Incognia’s content
Fraud farms enable bad actors to scale their illegal operations exponentially, but many platforms won’t know they have a fraud farming problem until they implement detection capabilities that can locate them. Andre Ferraz, CEO and Co-founder of Incognia, and Shawn Colpitts, Senior Fraud Investigator at Just Eat, answered a few of the most pressing questions about fraud farms, how they operate, and how platform administrators can stop them.
A single individual operating a single device may be able to commit fraud, but the damage they can cause on their own is significantly less than if they could scale to 10, 20 or 30 times the size. Today’s fraudsters are more advanced – operating with a complete team structure and a host of resources to help them accomplish their end, from dozens or more mobile devices to virtual machines to location and IP-spoofing tools.
Key TakeAways
- Fraud farms are large-scale operations wherein fraudsters use hundreds of mobile devices to defraud applications in different ways, from voucher abuse to new account creation to click farming.
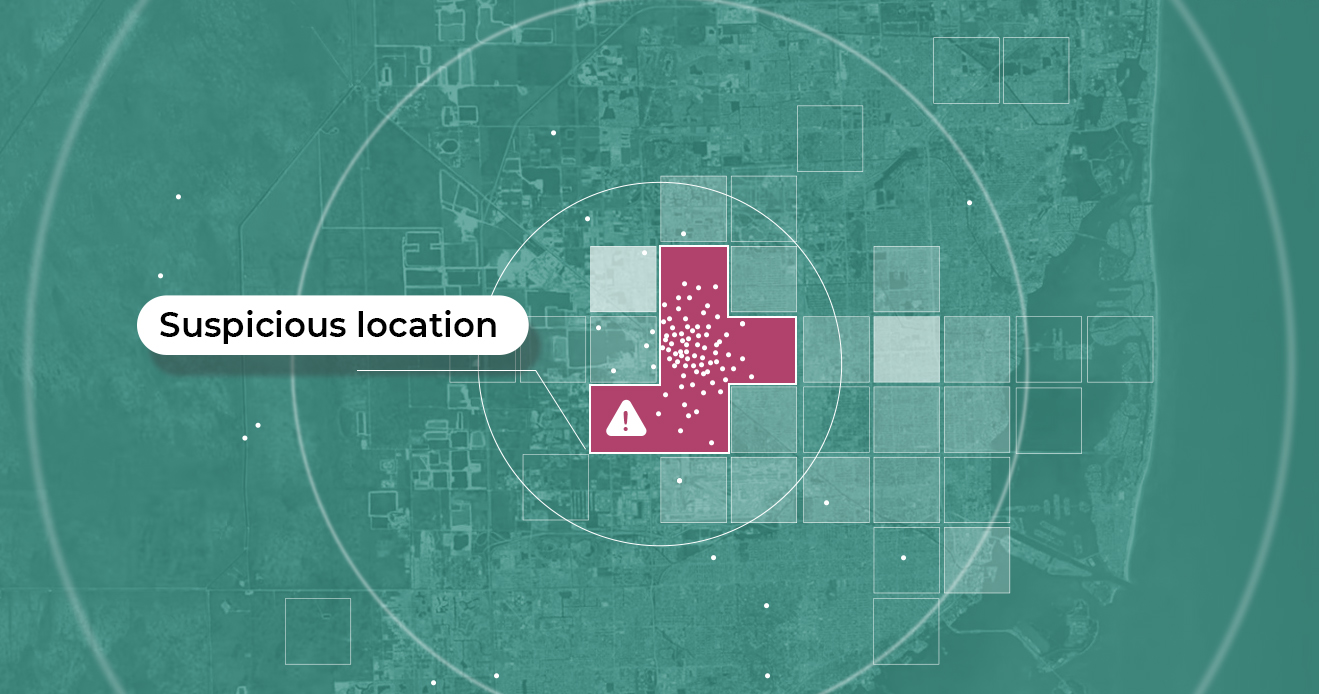
- Location is a powerful tool for finding and blocking fraud farms, but the location signals used must be both extremely precise, to avoid false positives, and spoof-resistant to prevent false negatives.
- Bad actors, including those behind fraud farms, are constantly pivoting to leverage new techniques. That’s why it’s vital for fraud professionals to stay up to date on the data, latest trends and innovative technology tools.
What are fraud farms?
Andre Ferraz defines fraud farms as “a professional and large-scale operation of devices used to illegally create or access multiple accounts in order to commit different types of fraud.”
In talking about the potential scale of these operations, Shawn Colpitts explains that to him, the term “fraud farm” refers to an organized team of people wherein each person is operating multiple devices each. “You need the ability to have one person working multiple devices at a time and typically at scale...In my opinion, it would be like three people, ten devices each, five devices each, maybe. And then you've got yourself a very simplistic Farm. However, as we're all aware, they can grow to be exponential in size.”
At their largest, fraud farms can encompass entire warehouses full of devices, and a single person might run scripts on up to one hundred devices at a time. With the exponential size comes the exponential ability to cause financial harm. For example, bonus abuse is a classic fraud use case for a device farm. While a single person making new accounts on a single device may not significantly financially impact a provider, a warehouse’s worth of operators and devices can make a sizable difference in the cost and ROI of a bonus initiative.
Shawn also commented on how fraud farms leverage social engineering to take over accounts:
Perhaps the most important thing is that fraud detection professionals remain as adaptable as the fraudsters themselves. Ferraz concludes by saying, “The most basic thing to do is, depending on the device ID signals that an application uses, fraud farmers may also be able to cut their costs by using virtual machines or a hybrid setup rather than relying solely on physical devices. Ferraz explains, “if the company is not leveraging a very strong device ID solution the fraudster can cheaply and easily use emulators, for example, and other tools, like App Tempering and App Cloning apps.” App cloners also don’t require a lot of technical expertise to operate–some can be found for sale on the Google Play store.
In cases where strong device ID does force fraudsters to use physical devices, they adapt rapidly to changing circumstances. As Ferraz points out, “These fraudsters are constantly pivoting.”
What fraud farms are used for
Bad actors, including those that run these device farms, are trained to follow the easiest money at any given time. Because of this, large-scale fraud farm operations don’t restrict to only one type of fraud.
For example, fraud farms may use multiple devices and cloners to commit bonus abuse, but there are also click farming to generate ad revenue, fraudulent account creation for money laundering, credential stuffing, voucher abuse, player collusion in iGaming, and more. The sheer scale of the operation can make what would be minimally profitable for a small-time fraudster, immensely profitable for the fraud farm operator–and maximally damaging for the target app. 
Ferraz explains, “The bottom line is that a fraud farm can be leveraged to commit many different types of fraud.” With Colpitts agreeing, “Thinking about it, you know, you have one device in your hand. How much damage can one person do with one device? You give that one person ten, twenty, thirty, forty, or fifty devices. Think about how much more they can do. And that's what these fraudsters are attempting.”
So, how can app administrators stop fraud farming and its consequences? Certain signals such as spoof-resistant location and device intelligence can help fraud professionals identify red flags in accounts, such as multiple accounts on the same device, a device using an emulator or GPS spoofer, an inappropriate number of accounts at the same location, and so on.
However, as Andre Ferraz explains, it’s important that fraud prevention experts taking this approach have technology precise enough to avoid false positives. GPS alone isn’t accurate enough to block bad actors at the apartment level–thus, other signals are necessary to use location for the identification and blocking of fraud farms.
"It's crucial to keep analyzing the data and testing new tools all the time…It's a nonstop job for everyone in the industry,” says Ferraz.
Shawn Colpitts concluded his comments with an interesting last thought: “My recommendation is to fight the fraud. Fraud farms are everywhere and they're doing all the different types of fraud that you can imagine….It's just a matter of the volume that they're able to put out and the amount that they're able to mask themselves. So if you can fight the fraud…taking care of the fraud farm shouldn't be so much of a problem to you.”
This blog post is a commentary on the webinar and Trust & Safety Mavericks episode #2. Listen to the full episode on your favorite podcast player:
This is an audio transcript of the Webinar: ‘Fraud farms - Identifying where fraudsters are’. You can watch the full webinar here, or listen to the podcast on Apple or Spotify.
Ronald Praetsch
Hi everybody. My name is Ronald. I'm the co-founder of About-Fraud, and I'm the host of our webinar today. Before we go into all the details to our speakers today, I have only one housekeeping rule. Please ask questions. Please be engaged to this webinar. We at About-Fraud try to find good topics, good speakers to share, good insights to you as our audience. So please be engaged. I can see already the chat is full with a lot of messages. So please ask your questions if you have questions.
And also Shawn is with us, he had some technical challenges on the way, but in time Shawn is here so we can kick this off now. So today we talk about fraud farms. Some of you already know what it is, some of you might have not really too much idea. That's why we have today two really interesting speakers who can give a lot of insights about what fraud farms are.
That's why first of all, I would like to welcome Andre from Incognia and Shawn from Just Eat. Andre, please do a short intro on your side, who you are, what are you doing that everybody knows, a bit of a background.
Andre Ferraz
Excellent. Thanks, Ronald. Everyone, it's a pleasure to be here. My name is Andre. I'm the CEO and co-founder of Incognia, which is a company in the digital identity space. I come from a computer science background, started my career about twelve years ago as a security researcher. For the past ten years I have been working specifically with location technologies. So it's a pleasure to be here and happy to talk about fraud farms and the issues around it.
Ronald Praetsch
Thank you, Andre, welcome. Shawn, your turn. Please give us a short intro about yourself.
Shawn Colpitts
Absolutely. Hey, everybody. I'm Sean, senior fraud investigator for the Global Fraud Operations Team at justeattakeaway.com. We look into all matters of account fraud for all the different stakeholders on our network, which ranges from anything from simple policy abuse right through to your credit card fraud schemes, including ATOs and the matter that, you know, these fraud farms do affect.
Ronald Praetsch
Perfect. Thank you and welcome Shawn. So as you can see, we have a mix of interesting speakers who can give some light and insights from different perspectives about fraud farms. And again, we always try to design our webinars so that you really get some takeaways. So I see my role really moderating and trying to get insights from Andre and Shawn, how you can really get something out of this webinar and really apply to more in your business or at least getting some more insights how you could prevent yourself or your company about fraud farms in this case. So on the right hand side you can see a few topics, what we're talking about today. But I think first and most important, really define what is a fraud farm and we have an interesting picture, and maybe Andre can kick this off and give him some more background. What is this picture about what is a fraud form? Is there any clear definition today? Or what's really about?
Andre Ferraz
Excellent. Yeah, this is a fun picture. So basically this is, as you can see, a bike with probably like 50 or even more phones. And the idea behind this is basically that you can run multiple instances, in this case I think it was Pokemon Go. So you could game the system instead of being a single player. Here you're playing as if you were 50 different people, and then at some point, as you in this case collect new Pokemon, et cetera, you could trade them and some people would even pay for those things.
So basically the definition of a fraud farm is when a fraudster, and usually a professional fraudster, someone that does that for a living, runs a large scale operation of devices to either create multiple accounts or access multiple accounts and commit different types of fraud. And usually that is also related to techniques that involve hiding the fraudster's true location, right?
So either hiding their IP address, hiding their true GPS location, and by doing that, they're able to be seen as if they were multiple people. But if you analyze, for example, the location data, you could identify that everything is connected to the same place, for example, or in this case, to the same bike.
Ronald Praetsch
Shawn, from your side, I mean, let me compare this webinar we really did some discussion about is there kind of a minimum number of devices which actually ending up in a Farm. If you have two devices or five, this is already a Farm, or maybe it's something different. Shawn, do you have a perspective on this, how you would classify a fraud farm? Is any kind of minimum amount of devices to actually call it a Farm?
Shawn Colpitts
That was a really good discussion that I wanted to bring up here. Three of us sat down and we were talking about what actually is that value, that number of devices used to actually say, this is a fraud farm. Can it be just several people there sitting at a couple of different desks around their dining room table with four devices in hand? Would that really be considered a fraud farm? In my opinion, no. You need the ability to have one person working multiple devices at a time and typically at scale. So even one person sitting there with ten devices, in my opinion, that's not really a Farm, because you also need a team involved.
So you're going to need several different people with multiple devices that they're able to action at one time or that they're able to function and work scripts on at one time. But again, you need that team effort environment. So putting a number on it is really hard to classify. In my opinion, it would be like three people, ten devices each, five devices each, maybe. And then you've got yourself a very simplistic Farm. However, as we're all aware, they can grow to be exponential in size.
There's many out there where you will see basically warehouse rooms full of the shelving units with phones all over them, one individual working about 100 phones going along, clicking as they need to on whatever ads, running whatever scripts they need to run to get the information that they need or the action that they desire. So they can be quite massive. But as for that minimum definition, that was a really fantastic discussion and honestly, we didn't really come up with a team consensus. I think you need at least three people probably running five to ten devices each to classify it even as just a low grade farm.
Ronald Praetsch
Yeah, and Dan just sent a question to the chat, and actually, that was my final question on this slide. I think we talked now about physical devices in the picture and also in our explanation. But Dan asked a good question, does a fraud farm really need to have physical devices or can you have any kind of virtual machines which maybe are even easier to emulate and have many, many more at the same time? Do you see in practice today, Andre, that fraud forms are more driven by physical devices or is there a specific trend or is it not even maybe hard? Is this now a virtual machine or really a device?
Andre Ferraz
Yeah, well, we see both and it really will depend on the applications, device ID technology. So some of them are using stronger device ID technologies. And in this case, this would force the fraudsters to create fraud farms that actually use more physical devices. But in some cases, if the company is not leveraging a very strong device ID solution, that might make it easier for the fraudster to use emulators, for example, and some other tools like App Tempering and App Cloning apps. So, for example, there's an app called App Cloner that fraudsters can just download on the official stores like Google Play and run multiple instances of the same application tampering the source code so they could also manipulate some of the system variables. So, yeah, it really depends on what you're using to recognize devices. But definitely if the fraudster is able to use emulators or App Cloners, it will make their lives easier and their operation will also be cheaper.
Ronald Praetsch
Perfect. I think that was a kind of a good kick off for our topic. Everybody with no idea what the fraud farm got at least an idea how it could look like. If we now going again into a bit more details, we already touched on some parts a bit, but again, here we want to dive a bit more details about what is really a fraud farm and why is this actually happening. And again, the fraud farm is not something which got started yesterday. So you have seen the example from Pokemon Go, which, I don't know, was running like a long time ago. So it's not really new, but I still believe not everybody is familiar with the term fraud farm. So I'm also wondering, is it something which comes and goes like in phases, or is it like a new wave right now, or is it just like something which exists in a long time, but now it's just more sophisticated because of better technology?
Shawn Colpitts
Yeah, I can start on that. Basically, as you mentioned there, with all fraud patterns, they go in waves, they go with whatever is working at the time and whatever is easiest to get that revenue, that desire, that final outcome. Fraudsters want to go with what's easy. And when it comes to these fraud farms, once you've got the devices and everything all hooked up, it is very, very user friendly for them to get anyone off the streets, typically to work it and to do these actions for them. One term that people might be very familiar with outside of fraud farms, because fraud farms can be used for a variety of different things.
But there's another term that is applied to fraud farms, which is click farms, which you may be familiar with, where they simply use the devices to click to basically generate ad revenue. They also use them to negatively affect companies where they know that this platform has good security and they will have these click farms attack these ads so that the company that's responsible for those ads gets a negative consequence from it and therefore end up, potentially, big picture, getting shut down. So right now we are seeing a wave with them. As things are advancing and technology is increasing, they're leaning towards these technical ways of doing things. And with a fraud farm, with all the different options out there that help them mask their identities, it becomes very, very difficult to actually track these down and shut them down. Like we can see them to stop the activity, however, then they just change things and they're out again. And with the sheer volume of devices that they have, the activity comes back in another storm. It's very hard to actually pinpoint the location and actually have them actioned to be physically taken down.
Andre Ferraz
Yes, I agree, it comes in waves. And these fraudsters are constantly pivoting, right? Like, if they get caught, and they're no longer able to run that specific operation, they'll try something else. If they're currently, like, defrauding a bank, they get caught. The next move is probably to start targeting ecommerce companies and then food delivery companies and then they might pivot to start doing jobs like writing fake reviews. So it varies. As you have access to these multiple devices, you have the manpower also to operate these devices. You can do multiple things, right, and usually they will try to find the operation that is more profitable, but also easier to operate. They're constantly changing and as Shawn said, it's hard to identify them physically because one of the main things they have in place is the use of techniques to hide their true location. Either spoofing IP addresses, spoofing GPS data. So that's what makes it more challenging.
Ronald Praetsch
Yes. And Paul from the chat already asked questions about the fraud types, but that's a good hand over to our next slide, are we actually going in a bit more details. I think that's also now the interesting part for the audience to understand, if someone is using a fraud farm, what is the use case without maybe sharing all the details, how it really could happen. But I think that's the interesting part. Also perspective from Shawn, how you see the delivery space, how this could apply. And I think Andre can give a lot of different use cases across the different industries, how fraudsters are using this. Maybe you can kick it off again with Shawn, maybe from the on demand space, maybe you can share one or two examples where you see in general fraud farms of really kicking in and having an impact on the operations.
Shawn Colpitts
Yeah, absolutely. In ecommerce, especially when it comes to high demand products, I hate to give this example because I love them, but Sony with the PlayStation 5, right,
these weren't just simple, some of them were just simple scripts running to try and sweep them up. But you had click farms on there, people going in multiple times, several devices, everything set up scripts running so that they only had to enter the specific fields and swooping up those PS5s. Another thing that you see as I mentioned is of course the click farms for generating ad revenue. You'll see them used for account creation, you'll see them used for many different things. Voucher abuses is another one where they try and use up coupons as fast as they can before anyone else can. There aren't a lot of things that seem like they would really, really benefit right off the hop, but sheer scale allows them to do so.
Ronald Praetsch
Looking at the fraudster, always the question is what is the target of the fraudster? Is it really reselling something? Is it ordering this one item or is it getting access to information which they could use later in the stage to actually catch out? So that's also always an interesting point, getting the mind of a fraudster, what is really the intention. And when we talk normally about the fraudster, it's something at scale. So if someone is using like the voucher twice or the coupon, so it’s not a fraudster directly, but if he does it at scale and making money out of this, that of course would be classified as a fraudster at the end. Andre, from your side, I mean, let's go top down and really trying to see what outcome use cases which you see from your side.
Andre Ferraz
Yeah, by the way, bringing an example from the food delivery space, one of the things we saw once was, and I think the fraud was really like someone was trying to throw a party for free. And it was weird. It was actually we found the location of the fraud farm and it was a union and they have ordered, I think, something like 200 orders on the food delivery platform. It was really crazy. We were able to block it, but they were trying to throw a big party that day. So it could vary, right? It could be like Voucher abuse. It could be, for example, in the financial services industry, we see a lot of fraud farms being used to create multiple accounts so they could sell these validated accounts for money laundering purposes, like money mules, etc. So we see a lot of that in the financial services industry. When it comes to online gaming, for example, collusion is a huge problem. So one of our partners is a poker game. And what was going on was that people would get together to join a table so that they could manipulate that game. And there was cash involved, right? So if there is a poker table with like five people and three are actually playing together, they could game the system. They could basically take all the money for themselves. So what they were doing was they were using fake GPS technology, so they would show up to the poker game as if they were in different locations, but they were actually in the same room. So we started flagging these locations so they would block not only those devices, but also the place in which they were operating so they could not access or create new accounts. So it varies a lot.Basically, this is, I would say, probably the root cause of most fraud types, because when you're able to establish an operation like this, you're able to run these fraudulent activities at scale, right? And this is where companies face real problems, is when a professional is able to automate and scale up their fraudulent activity. Because if we consider like the fraud that spread out with individuals, like a person that just wants to get a ten dollar coupon to ask for food. At scale, that could be a problem, but if you compare that to a professional operation that already knows how to do that same thing much more quickly using multiple devices, emulators, et cetera, that could hurt more.
Shawn Colpitts
I know we have Pokemon Go to thank for a lot of that GPS spoofing technology that's out there as well, but I'm wondering how far it goes to actually the buildup to these fraud farms. Was it this Pokemon Go gentleman on a bike with all these devices that led to other fraudsters being like, hey, wait a minute, I can use that?
Andre Ferraz
Yeah, there's actually an issue that goes back to actually the implementation around the developer platforms for these mobile operating systems. So both Apple and Google, they have implemented a feature for developers that enables them to change their location for testing purposes. Right. So if I'm working for a global company, and this company has operations in multiple countries, if I'm currently developing like a feature for certain geography, which I'm not located in, how would I test it? So if I'm a developer at, let's say Uber, right, and I'm currently in the Bay Area, but I'm developing a feature for the Indian market, how would I test that? So the platforms have enabled for developers while they are on developer mode to change their location.
For that person, it's actually a feature. But then that feature started being exploited by the bad actors as a way to hide their actual location. So, for example, if you go to the App Store or to Google Play and you type fake GPS, you're going to find hundreds of apps that give you these capabilities. And the only thing you need to do is actually to turn the developer mode on your phone. So it's not even something that you need to be like a hardcore hacker that is going to bypass the security on the device. That's actually a feature that is embedded on the operating systems. So that led to things like the GPS spoofing on Pokemon Go, which was basically where all this thing has gained a lot of scale and then fraudsters starting to identify that opportunity.
So they started using that for like as drivers on ride hailing apps. They started spoofing GPS for that so they could be like at home, for example, accepting multiple rides. They would never show up, but they would still make like $5 or $6 because the consumer didn't find them, but actually they were not there. So anyways, it's a feature that turns into a security vulnerability.
Ronald Praetsch
I have a question to Andre. Can you detect from a technology point of view if someone is on a developer mode or not?
Andre Ferraz
Yes, you can detect that. You can also detect things like App Cloners and App tempering tools, instrumentation tools, emulators. So the detection is possible. But one of the challenges here is that not necessarily some of these things are a real problem. So developer mode, for example, my phone is on developer mode because I'm a developer, and I'm not a fraudster. So should I be blocked because I happen to code sometimes? Not necessarily, right. So you have to leverage other signals to determine risk. Not only that, otherwise that could lead to high false positive rates.
Ronald Praetsch
Yeah, makes total sense. Joe asked a question about P2P payments and he gave two examples with sale and cash apps. I think there are many, many more. We also have on this slide the finance sector. Do you have any insights, Andre, from your side if that's the case right now with P2P fraud, that fraud, or let's say fraud farms or this kind of device moving is really helping fraudsters to optimize operations?
Andre Ferraz
Yeah, a fraud farm could contribute to this type of fraud in two different ways. The first one is to create accounts at scale so you could receive the money, right? So that's evidence that that fraud operation is later going to be used for scams once you have a number of accounts that could receive the money. And also these fraud farms could also be used for different things. Like for example, if someone is social engineering users to convince them to give away their credentials, one of those devices will be used to access that account, for example. And another thing is that fraud farm could also be used to run like more basic type of attacks that are usually leveraging more like emulators for credential stuffing, using bots.
So you don't really need to have multiple devices to do that, you just need to have multiple instances of emulators to do that. But most companies already have better protections for this type of thing. The last one that I would mention, which is more challenging is the unauthorized push payment fraud. Because in this case the actual, like, the legitimate user is performing the transaction. So the fraudster is calling you and convincing you to transfer funds to someone else from your phone, right? So everything looks good, it's your phone, it's ready, authorized to access your account, it's your–like if they're using Biometrics for example–it's your biometrics. So that's a lot more challenging to identify and block. But those are the different types of things that we're seeing in the finance space and that could, once you create the ability to identify fraud farms, you can start stopping them. So the first two I would say are more root causes for the others. You have to have an account to receive the money.
Ronald Praetsch
And I think you touched an interesting point. I think this push payment fraud in general is challenging around the world. Of course there are some markets more leading with the rollout of push payment. And I think Brazil is a good example we’ve picked where actually I think even the regulator or the government took actions that so far I know we can only do the transactions in a certain time frame, not in the middle of the night anymore to actually minimize the fraud. So on one side, push payment can drive convenience, on the other side it gives lot of new avenues for fraudsters to really exploit this kind of new technologies or identifying better ways of getting faster to the money.
Andre Ferraz
Yeah, and by the way, that change that the central bank in Brazil implemented to block like big transactions during the night didn't work, didn't work at all. Like the fraudsters simply started working during the day. So yeah, that's challenging. Other techniques are now in place to address that, but blocking specific times of the day is not really what you want to do.
Ronald Praetsch
I think there's one question from Bushgard that's maybe an interesting question. In general, can someone use a fraud farm also to make fraudulent phone calls. I don't know, but maybe Shawn, Andre, you have an idea if that's also the case, that this kind of phones are used to make fraudulent calls, maybe with a certain technology to reach a lot of people at the same time.
Shawn Colpitts
Myself, I haven't honestly heard of the phone call operations within fraud farms. But realistically, thinking about things at scale like this, there's a good possibility that absolutely. I don't know if I've seen anything like this reported to him, but it makes sense that it could be. You have a massive scale of devices and just simply reaching out and having those connections. We've got multiple people, multiple devices. One connects. Okay, well, they pause and they work on that while the others are still cycling through their devices, trying to get someone to connect.
Andre Ferraz
Yeah, I've seen a fraud farm operating as if they were actually like a call center. They would have people that were dedicated to calling people while others were on the other devices, like accessing the account. So this case was in, I think it was in Rio de Janeiro, Brazil. And just sharing curiosity here, the person who was running this operation was the daughter of, I think, a rap music celebrity. Was pretty weird when that went out to the press, but they had hundreds of people calling others to perform social engineering scams. So it was a pretty large operation and they had an entire building filled with people doing that.
Ronald Praetsch
I think there's one more interesting question which came in from Gabriel before we jump into the next one. I think still like a lot of services in the finance space and also certain other apps are using OTPs. So now the question I think is good, can fraud farms be leveraged for generating OTPs and account takeover? Is it something which is linked to each other or is OTP helping to protect against the fraud farm or even helping?
Shawn Colpitts
Absolutely, fraud farms could be used in the same way that Andre was talking about there. Obviously, you have the multiple people with the multiple devices and making contact. So we know with OTP getting those, the fraudsters try and access the account, they then have the push sent and then they contact the person on the other end, like the customer at the same time to try and retrieve that password. So absolutely, it could be. And they don't just do so for the OTP pushes. They will do so just as also discussed, for the credential stuffing attacks themselves, they have all the different devices running scripts, people there manually doing inputs as well, trying to access these accounts on that.
Andre Ferraz
So, absolutely, yeah, I would say that the bottom line here is that a fraud farm can be leveraged for any different type of fraud. The main thing is here with a fraud farm, you're doing it at scale, right? So if you think about any type of attack that you're suffering or you have suffered in the past, a fraud farm could do that at larger scale. So it's just the way that these criminals, they organize themselves to work together as a team.
Shawn Colpitts
It's just that simple. Thinking about it, you know, you have one device in your hand. How much damage can one person do with one device? You give that one person 10, 20, 30, 40, 50 devices. Think about how much more they can do, and that's what the fraudsters are attempting.
Ronald Praetsch
Yes, again, that's the scale. Good. I think we got some interesting questions. Thanks for this. Let's go into the next slide again. We already touched part of this, but again, here it's also for the audience, the summary. What are the topics which fraudsters using to really do this kind of location spoofing at the end of the day, which ending up in the platform? Maybe Andre from your side, but also maybe if you can maybe highlight what is maybe like a trend, is a certain technology more used than others, or is there anything new coming up right now? And also the interesting part often which I get from the audience, also my consulting topics, how much you mentioned also before with the modes, like the developer modes. So how much is also driven by Apple and Android to maybe enable or disable certain topics? Or do they even care about this, that devices can be misused for certain purposes?
Andre Ferraz
Perfect. Yeah. So talking briefly here about the techniques that are used by processors to spoof your location or hive your location. The first piece is related to IP related geolocation. So you can locate a device using its IP address. But there are two issues here. The first one is simply around accuracy. So the data, usually the granularity, is going to be to the city level, so you'll be able to identify, okay, this person is logging in from San Francisco or New York or any other place, but you cannot really understand in which specific neighborhood, for example, or street or even apartment this person is operating from. So it doesn't help a lot on identifying fraud farms because most of these fraudsters already use some techniques to change their IP address. They could be using, for example, Proxies or VPNs or browsers like Tor. So there are multiple ways in which fraudsters can do that, and they actually already do it as a standard, even if they're operating as a single person. Right? If they build a larger scale operation, they're more organized, they have a team, they have multiple devices. It's very likely that they're doing this.
So leveraging IP addresses might not be the best tool to identify and block fraud farms. The other thing is when it comes to mobile applications that have more capabilities related to capturing location information, when this app has access to location services, in this case the GPS of the phone, the issue. Here is what I was talking earlier about this feature that both Android and iOS have enabled developers to change their location while on developer mode, right? So this feature is being exploited by fraudsters using GPS spoofing apps. So you can download on the App Store, you can search for fake GPS, you're going to find multiple apps that enable you to do that. So one important thing you have to do is to map these applications, detect them and block users that have them on their devices. Otherwise the risk of having these users spoofing GPS is very high. And then finally emulators instrumentation tools and app temporarily. So the app that I was talking about earlier called App Cloner is an example of that. With this, the truster can run multiple instances of the same application on that same device and they can also tamper with some specific things like for example, changing the GPS coordinates from that application so you would be recognized as being somewhere else. So the first and most basic thing that you have to do is to verify for those things. You have to have a database of these GPS booking apps, app Tempering Tools. So if you detect that, you can either block that user or challenge that user to share more information so you can trust them.
And then finally, there is another thing more specific to mobile applications, which is that these apps can also access other sensors. And this is actually where Incognia specializes in, which is mobile apps can also access things like Bluetooth signals, WiFi signals, right? Cell tower ID. So by leveraging order signals to locate that user, you can find when there is a mismatch between the GPS coordinates and these data points. So for example, one of the things we do is we work with a concept we call location fingerprinting. So for example, right here where I'm located, there is a unique set of WiFi signals and Bluetooth signals that you cannot find anywhere else. So we create a fingerprint for this place and if we identify these signals, we know where they're located. And if that doesn't match the GPS coordinates, we know that the GPS spoofing is going on.
So that's not a way to detect that. But to do that it is a lot more complex because you have to build a huge database of all of the WiFi, routers and Bluetooth devices all over the world and keep it updated. So you need to have a lot of scale to do something like that. But the most basic and thing that you can do is monitoring for these five things here on the screen [Proxies, VPN, Tor, GPS spoofing apps, Emulators, Instrumentation tools, and App Tampering]. If you do that, you can at least stop the more basic form of location spoofing.
Ronald Praetsch
But maybe also the question to Shawn is that that easy to implement because of course we also want to see what are the low hanging fruits for the audience to get started. Of course, some of these data points are easier to detect, some others are a bit more challenging to really get the data and updating the data and detecting this in the right way. Does any insight Shawn from your side what you have seen, what is easy to implement and how would you get started?
Shawn Colpitts
Yeah, as you were saying, a lot of these technologies aren't available to everybody and being able to maintain and keep up on the advancing trends and everything that keeps getting released. Like as soon as there's one GPS boothing app, there's another one, and another one, and another one. So it is really difficult to keep up with these things. And unfortunately, when it comes to fraud farms and just fraud detection in general, you have to attack the fraud. There's a lot of good signals that indicate that this fraud is happening from a farm, but you really can't tell if it's a farm or if it's someone running an emulator in a lot of instances. So you really have to attack the fraud using some of the attributes that you see. So for example, when you're picking up on human patterns, for example, let's say account naming patterns, email patterns, those kinds of simple things stand out because they're following a guide where they need to push out as much as possible. So they're going to fall into that trap of patterns. If you're noticing, again, locations showing up for the end user or input or very, very slight variations. So you see over a short succession of time, 111 Main Street, 112 Main Street, 113 Main Street. They fall into that because they're trying to avoid detection, but also push out as fast as they can.
Randomness comes into play with details. When it comes to the technological side, they're rotating through IP addresses, so it's hard to see. A lot of times you'll see that the provider is the same along with the behavior. So you'll see the behavior to match with that. You always need a multiple prong approach. Like Andre mentioned, you cannot just focus on this person's in Developer Mode. So I should stop them. You always need multiple prongs to your attack, so that developer Mode, for example, is a good indicator that you can pick up on. But further than that, what are they doing? They may be in Developer Mode, but are they using a VPN? Can you see that? But again, being a developer, that's not really going to help you too much. But the credit card that they're using, the name that they're using, the phone number that's using Address, any other indicating that factor that you have, is it matching to other activity on your network?
It's really a pairing game in these instances because of their velocity, because we can't stop them without a lot of great technology like this. At the get go, we need to wait for something to happen so that we can pounce on them.
Ronald Praetsch
Yeah, I think if I would summarize the big takeaways, you always need a layout approach. There's no golden bullets involving everything. But again, this is like at least one area to consider when you're building your profile around your transaction of your customer. We already got some more questions in, but I would like to finalize the next two slides. We have some more content, and then we can go through the open questions. So to the audience, please feel free to send your questions. We're going to finalize the next two slides of the content, and then we're going to focus on your questions. I think the next slide is an example from Andre again, to illustrate how a fraud form could look like.
Andre Ferraz
Excellent. Yeah. In this case, this was a voucher abuse type of issue. So it's a gaming company from India. They offered credits for new customers that were onboarding to their application. And in this case, we have detected 166 devices creating accounts from a single house. We blocked not only those devices, but also the place. Right. So we got the location fingerprint, we blocked that place. And one thing you need to be very careful with is you should not do this if you are relying only on GPS information. The reason why is because GPS is pretty good for navigation. For example, if you're using Google Maps to go from point A to point B, it works well. But the issue is that if you're using it for this type of activity of, like, blocking a particular place, that could lead to very high false positive rates. So, for example, if there is a fraudster operating from a high rise building in which there are other, like, hundred apartments, right? That means that if you block the GPS location, you're blocking the fraudster. But everybody that lives nearby and those people, they have nothing to do with that fraudulent activity. Right.
So if you want to use location data to block fraudsters, and to block locations more specifically, you have to be using something that is more precise than GPS. So you block the specific unit, you would block the specific apartment within that building, but the other people that live nearby will still be able to use the service. So that's an important consideration here, because there are many fraud farms out there. If you detect them using GPS data, that would be a signal. But if you're using data that is not super precise, I'd say 10ft accuracy or so, you should not be using that to block entire locations, because that would block a lot of good people.
Ronald Praetsch
I have a question to Shawn. Would you recommend today in general, plugging or blacklisting general information? I think in the past a lot of tools or companies did a lot of blacklisting. But what I see as a trend in general, it's not really happening anymore, that people blacklist this kind of IPS or blacklist zip codes or blacklist certain elements. Because then again, it's one data point and then you potentially can impact many good customers. Shawn, how are you dealing with blacklists in general? Are you still dealing with blacklists or a very specific case, this one credit card or this one email address. Unless it's kind of general information like a GPS or an IP.
Shawn Colpitts
Ultimately we don't want to have to blacklist anything. And when it comes to larger scale information such as an IP, which can affect a lot of people, we tend not to do that. So for example, the small scale fraudsters, say, who are doing like policy abuse or refund return abuse or something like that, absolutely. They may get to a point where we're just like, you know what, let's just block them from getting orders, period, block one of their attributes that are unique to them. But ultimately what we want to do is battle the fraud. We don't want to attack a specific individual or a small organization. We want to stop the fraud from happening in the first place. So we look for attributes that we can use to counter it from happening at all. Regardless of just one specific prolific individual. Myself, I'm personally against blacklisting anything. I'm a firm believer that if you can stop the root cause, you stop it all across the network as opposed to one single individual. I don't think that's the proper route to take.
Ronald Praetsch
Thanks for your perspective. We have one more slide where we go into a bit more tech. So if we keep this condensed Andre, then we have some time for some good questions.
Andre Ferraz
Perfect. I’ll be brief here. So the first piece that we explained here was around the device integrity checks. So basically analyzing the device to understand for example, if they're using VPNs, proxies, they're trying to hide their IP address. Second piece is identifying things like if that device is actually an emulator, if it's rooted or jailbroken. So those are also important checks. If it is on developer mode. And then finally identify the other things that we've mentioned here, like the presence of GPS spoofing apps, app tempering, instrumentation tools, et cetera. So this is the most basic part that you need to address so you have access to this data and you can analyze to identify if there is higher risk of fraud. Second thing is what we call the watch lists. So once we receive feedback from our customers that there was confirmed fraudulent activity from that device or from that location, we would start flagging this as OK, this is the second time. This is the third time that we see activity from this device or location. And then our customer can decide if they're going to approve that transaction or not, if they're going to block that user or not. So flagging these accounts, devices and locations is important.
But again, if you're flagging locations specifically, you got to make sure that you are identifying it with very high precision. Otherwise, if you block the location, for example, using GPS, you could block an entire building. High false positive rates, a huge problem for the business. And finally, the other thing we do is around checking the other sensors like WiFi, Bluetooth, Cell, Tor, IDs, GPS. So in that way we can get a more granular information about location. Right? So in this case, the average accuracy of the location technology here is around 7ft or two and a half meters, which is a lot more precise than GPS even within a building. For example, this enable us to identify which floor that device is. And that helps with this type of scenario of identifying a fraud farm. So you're not only identifying a GPS lat long, you're actually identifying an apartment within a building. In that way you can be more targeted on your analysis.
Ronald Praetsch
Okay, I just want to give a few sentences to Tom. So Tom is asking about once the fraud farm is identified, can the data be shared in an industry to actually reduce the risk? I think that is often a good question, how we as an industry can use the data to help each other and minimizing the exposure for the others. I think that's often the role of providers. We actually have this network of data and as Andre just mentioned, once device or location is confirmed or added to the watchlist, the other people in the network I assume, can benefit from this and actually the signal gets higher and potentially minimizing the risk to get exposed by this kind of devices. But again, that's something in general, the industry providers being this kind of man in the middle, collecting the data and actually sharing this.
We have only a few minutes left, but I would like to pick one interesting question from Paul. So Paul is asking, in the UK, most banks have devised solutions that can spot rooted or jail processed devices as well as GPS locations. Are you saying that now technology that can circumvent these defenses? Maybe it's a question for Andre maybe to challenge this or giving advice or giving insights. How is it done today?
Andre Ferraz
Yeah, well, if you're using GPS data for fraud prevention purposes, without a strong GPS spoofing detection, that's not going to help you. So you need to use both in conjunction. If you're leveraging location signals to identify either fraud or good patterns from good users, you should also have a GPS spoofing detection technology. The reason why is, as I explained before, the operating systems have enabled developers to change their GPS coordinates and identifying only if the user is on developer mode might lead to a lot of false positives. So as Shawn was mentioning earlier, you need to look at many different variables to determine if that's a good user or not. Otherwise the developers are making a lot of money today. You might lose a lot of good customers if you want to block all of them.
Ronald Praetsch
Perfect. I think that's leading us to maybe recap, maybe shown first on your side. Any kind of last insights? Last advice to round it up from your side, that we just rounding up and finalizing this topic from your side.
Shawn Colpitts
Yeah. Not so much technical dive as to what Incognia has put together here. Being able to identify the specific location down to the point of an apartment is fantastic. And the good thing about having that kind of a feature with fraud farms is the fact that they're stationary. Right. It's not someone who's using a device here and then they're going to use it from work or they're going to use it at the mall. They are stationary to that location because that's where their setup is. So until they decide to disassemble and potentially move somewhere else, that location is where that activity is happening. So that is an extremely good feature to have. It's not available to all of us. So really my recommendation is fight the fraud. Fraud farms are everywhere and they're doing all the different types of fraud that you can imagine. They're not sticking to just one type of fraud. It's just a matter of the volume that they're able to put out and the amount that they're able to mask themselves. So if you can fight the fraud and get the fraud, taking care of the fraud farm shouldn't be so much of a problem to you.
Ronald Praetsch
Thanks, Shawn. Andre, any last words on your side to the audience?
Andre Ferraz
Perfect. Yes. Shawn's point was, he nailed it. It's hard to identify fraud farms. It's not easy. They have multiple ways of hiding their true location. So if you attack the fraud, that's the first step. I agree with Shawn. If you have the resources and if you have a large operation where you can afford, for example, having more sophisticated tools around, identifying, for example, GPS spoofing and getting to very gray location information, you're going to be able to address this. But the most basic thing is to keep, like, analyzing the data and testing tools all the time. If you solve the current fraud issue that you're facing right now and you bring it down, fine, you're going to feel good for a few weeks or months, but the fraudsters are going to figure out a way to find another attack that works. So you need to be constantly analyzing the data, monitoring it, testing new tools. This is a cat and mouse game and that's the reality. So you need to be watching webinars like this and learning about new techniques all the time. It's nonstop work for everyone in the industry.
Ronald Praetsch
I think that's a good last word. That's why fraud fighters like us exist or in the industry on the provider side, on the merchant side, to really stay up to date and really trying to find a new way to protect the business on the other side. This is also the exciting part, why we are in this industry, because it's always something new. And yeah, I mean, that's why we're doing this webinar as well, to give you updates, give you insights to learn about new topics. And there are so many topics. So it's really interesting to see what we're doing next and also where the fraudster is moving next and what is the next big trend. So, first of all, big thank you to Shawn for joining today. Big thank you to Andre for joining and being part of this. Big thank you to the audience and joining and being active and asking questions. We still have questions to answer today. We're going to see how we provide feedback to all of you with some more insights that we know. Not losing your good questions here. Again, thank you and have a nice day. Bye bye.
Andre Ferraz
Thank you. Bye.