Recent posts

Five Ways Fraudsters Spoof Location
Location spoofing is now a standard technique used by...

How should location fit into a risk based authentication strategy?
How to implement frictionless risk based authentication...
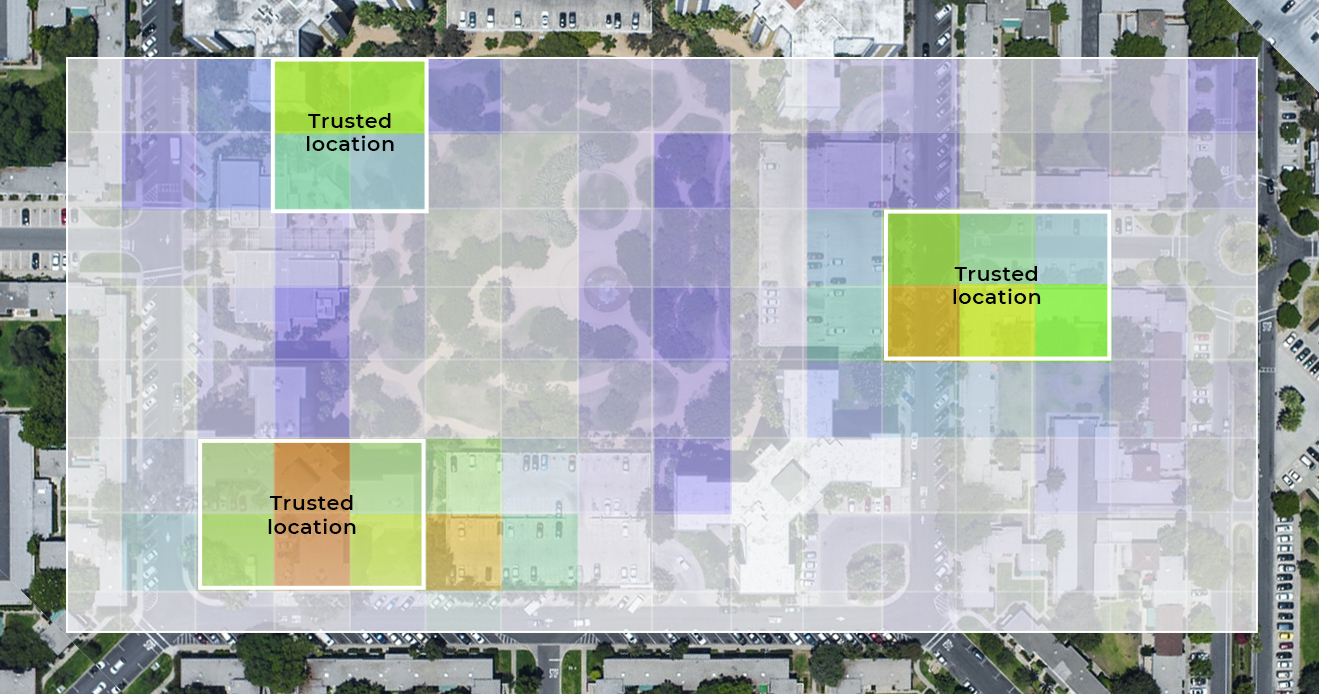
Account Takeover Prevention Using Location Behavior
Strong Account Takeover Prevention could be achieved...
![Featured image for Prevent Mobile App Fraud [The Most Expensive Form of Identity Theft] resource](https://www.incognia.com/hubfs/%5BFEATURED%5DPreventing%20Mobile%20Application%20Fraud%20%5BThe%20Most%20Expensive%20Form%20of%20Identity%20Theft%5D.jpg)
Prevent Mobile App Fraud [The Most Expensive Form of Identity Theft]
Application fraud is a billion dollar problem for financial...

