Privacy considerations for location data
With the widespread use of location technology by apps, we are becoming increasingly accustomed to the benefits of location-based services, including real-time navigation, ride hailing, and food-delivery. Google Maps, Uber and GrubHub are just some of the go-to apps that are making our lives easier and more convenient. But collecting, storing and working with location data raises important considerations regarding user privacy that need to be addressed.
If collected and stored irresponsibly, location data can reveal a person's real world identity and behavior. When location datasets fall into the wrong hands and are linked with personally identifiable information (PII), either from internal or external data sources, user privacy can easily be compromised. This is why Incognia takes a privacy-first approach to location.

Our privacy-first approach to location
At Incognia, we view ensuring the privacy of location data as paramount. In fact, user privacy is where our founders started, over ten years ago, when they designed and developed the core location technology that is now in use in 200M+ devices.
Incognia follows four core pillars in its protection of location data and user privacy.
-
01
We put user privacy first
We follow the 7 fundamental principles of Privacy by Design as the foundation of our product design, implementing privacy protection from conception to final use of our products and solution.
-
02
We keep PII and location data separate
We believe the best way to keep personal information and location data separate, is not to collect any data that can directly link to identity. At Incognia we focus on encrypting and protecting the location data we collect, and intentionally do not collect additional PII.
-
03
We use proprietary location anonymization technology
We focus on hashing and encryption to protect the location data we collect, and intentionally do not collect additional PII. Other techniques we use include probabilistic set structure, differential privacy, and k-anonymity, bringing the data closer to full anonymization.
-
04
We are mindful of data retention
Just because data can be kept, doesn’t mean it should be. At Incognia we follow the best practice of only keeping data as long as it is actively used. If data isn't stored, it can't be stolen or contribute to downstream fraud caused by stolen credentials and PII.
How does Incognia capture location data?
Through network signals and device sensor data, Incognia creates a location fingerprint, or private digital identity, based on location behavioral patterns unique to each user. Incognia location technology is very precise and unlike GPS is not susceptible to spoofing.
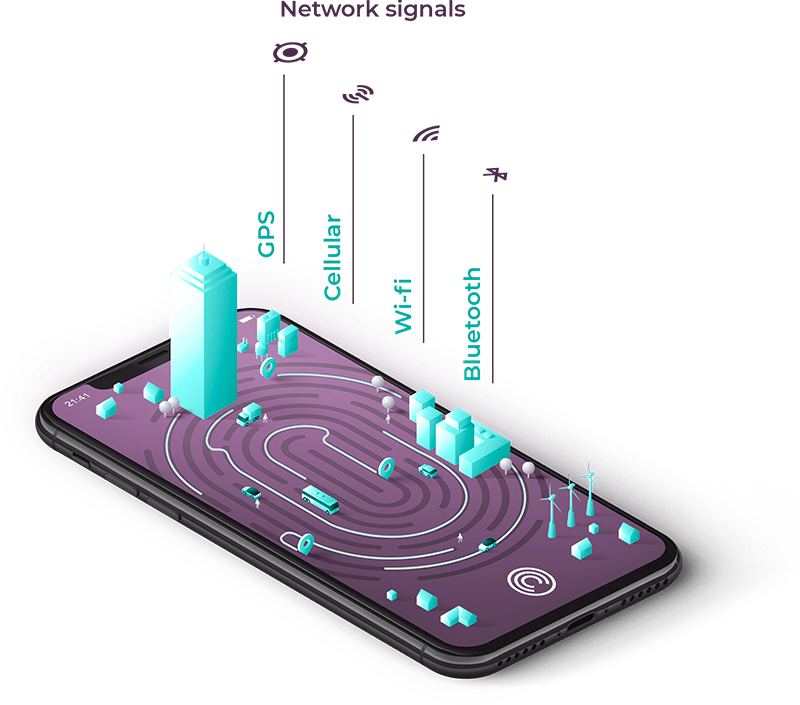
Understanding smartphone location technologies
How we implement Privacy by Design
Incognia treatment of location data
- We consider location data as extremely sensitive, and treat it accordingly, applying extended anonymization techniques to obscure and protect all location data.
- We continue to invest in research on homomorphic encryption, multi-part computing (MPC), zero-knowledge proofing and differentially private data structures.
Location data versus location context
- Incognia does not store the actual user's location history, only an anonymized version.
Handling sensitive locations
- Incognia infers certain locations that may have a sensitive context e.g., home or work and applies proprietary anonymization techniques to encrypt and anonymize the location data.
- We use a trapdoor function on our identity proofing solution so we are able to prove the user's home address e.g., for a loan application, without having knowledge about the address itself.
Implementing Privacy by Design eBook

One Page
Incognia Privacy and Data Protection
Download this One Pager to learn how we protect user data, what data we do collect (and don't collect), how we ensure data security and how Incognia compliance with laws and regulations and additional certifications.
How to know which apps are using location?
-
Android
Go to Settings > Apps > App Permissions > LocationView the apps that could require location access on your mobile device and set permissions.
-
iPhone
Go to Settings > Privacy > Location ServicesView a list of the apps using location technology and set permissions.