Recent posts
![Featured image for Fintech Mobile App Friction Ranking [Login Authentication] resource](https://www.incognia.com/hubfs/featured-image-blog-mobile-app-friction-report-v2.jpg)
Fintech Mobile App Friction Ranking [Login Authentication]
Incognia Mobile App Study ranks Klover and eToro winners...

Mobile Authentication - Security and Friction Rankings
Learn how the different types of mobile authentication rank...
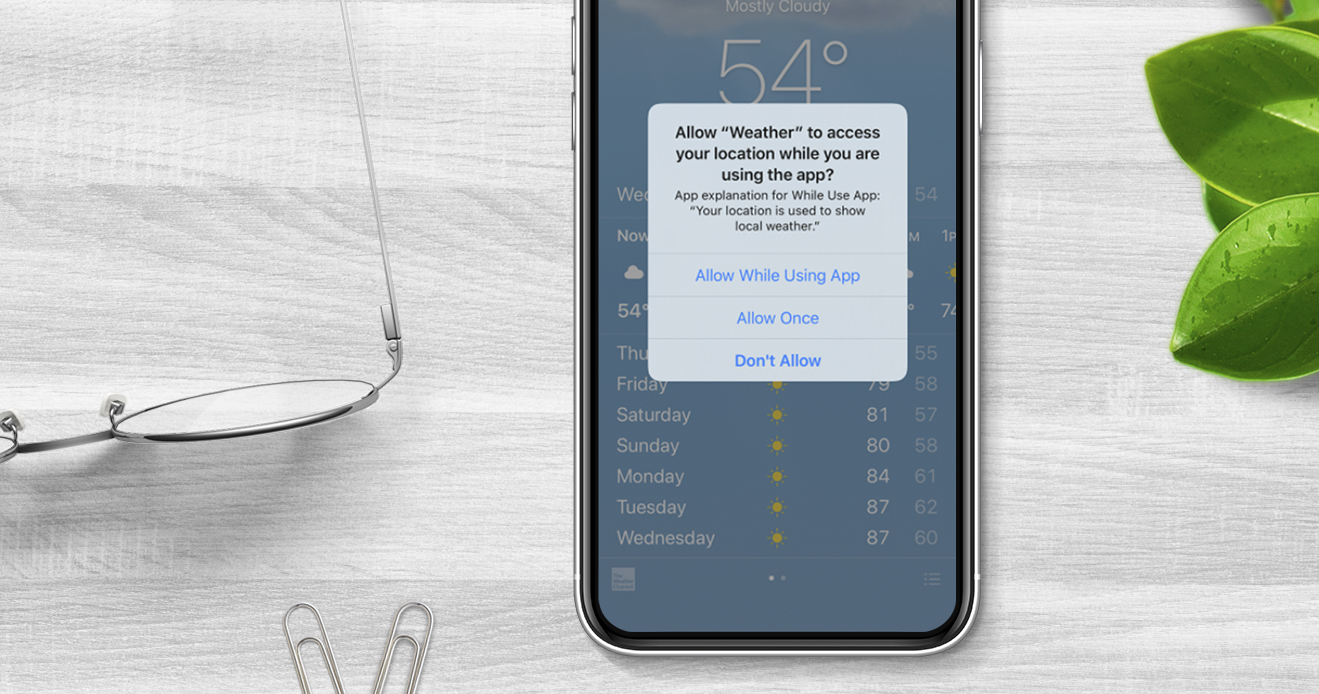
The secret of increasing the opt-in rate on your mobile application
Learn 5 things to know about Location Permissions, an ebook...

Solving the digital identity problem for mobile and beyond
Digital identity is a challenging problem and far from...

Why Location is Hard to Get Right
Applying location technology to mobile fraud prevention is...

Why Precise Location Matters for Mobile Fraud Prevention
With 50% of transactions happening on mobile devices, and...

