Recent posts

Five Ways Fraudsters Spoof Location
Location spoofing is now a standard technique used by...

How should location fit into a risk based authentication strategy?
How to implement frictionless risk based authentication...
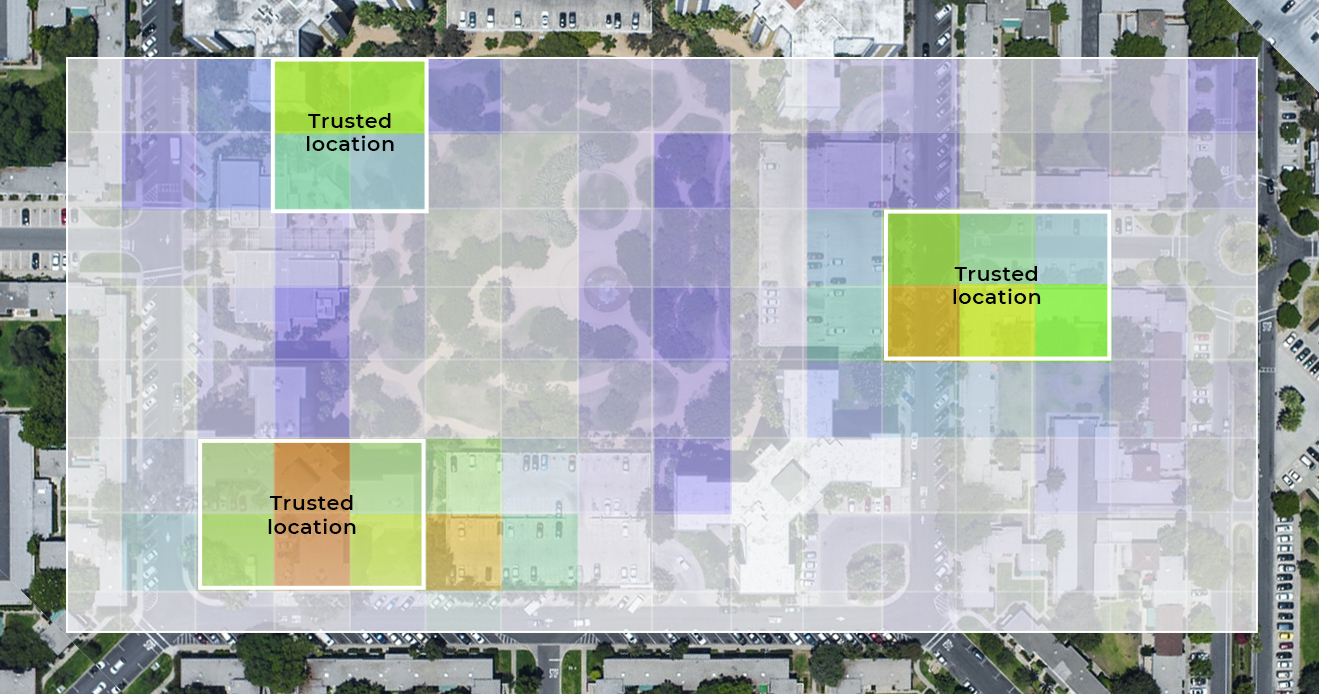
Account Takeover Prevention Using Location Behavior
Strong Account Takeover Prevention could be achieved...

Incognia: A Great Place to Work
Incognia was recently certified as a great place to work by...

Real-time address verification for mobile
With increasing mobile adoption, use of real-time address...

Global QSR Approves More Mobile Transactions with Incognia
Incognia dramatically increases approval rates for mobile...

