Recent posts

Device authentication for fighting fraud: when your phone is your new password
Learn about device authentication as a security measure,...

Incognia is featured in the best authentication solutions on Cybernews
The experts from Cybernews recently took notice of our...
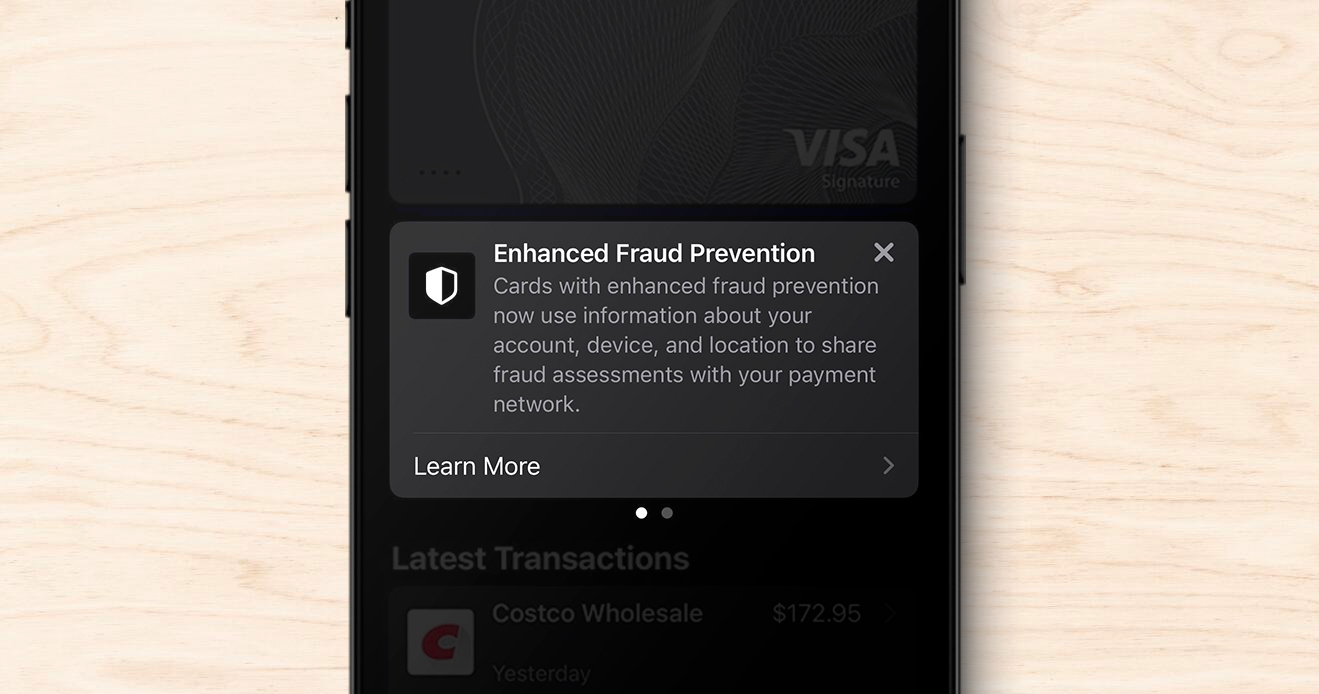
Apple announces use of location for fraud prevention
Apple Pay is now using location for fraud prevention. This...

Authentication Mobile App Friction Report - Crypto Edition
A review of authentication friction in top crypto apps at...
Why it's time to stop relying on static credentials
Static credentials are vulnerable to exposure via social...

