Recent posts

How App Cloners are Becoming a One-Stop-Shop for Fraudsters
Take a deep dive into the rise of app cloners and what...

3 Ways Multi-Sided Platforms are Defeating Ban Evasion
Explore how multi-sided marketplace platforms are tackling...
Death by 1,000 Cuts: Why Even “Small-Time” Fraud Matters on Food Delivery Apps
Dive into the impacts of seemingly small-scale fraud on...

ELF: The Persistent Signal Fraudsters Can't Erase
Learn about the threat of recurring fraud and the...

Why Solving Multi-Accounting Is Worth Your While
Learn about the return-on-investment potential of tackling...
New Account Fraud: Are You Missing This Critical Ride-Hailing Fraud Problem?
Learn about the impact new account fraud has on ride...

Fraud Prevention Doesn’t Kill Growth, Multi-Accounting Does
Fraud prevention is sometimes seen as hurting growth, but...

How to Make the Case for Fraud Prevention With Different Departments
Learn how to communicate the value of fraud prevention more...

Banned Users: Why Fraudsters Aren't Afraid of Being Banned
A closer look at ban evasion, why it's a problem, and how...
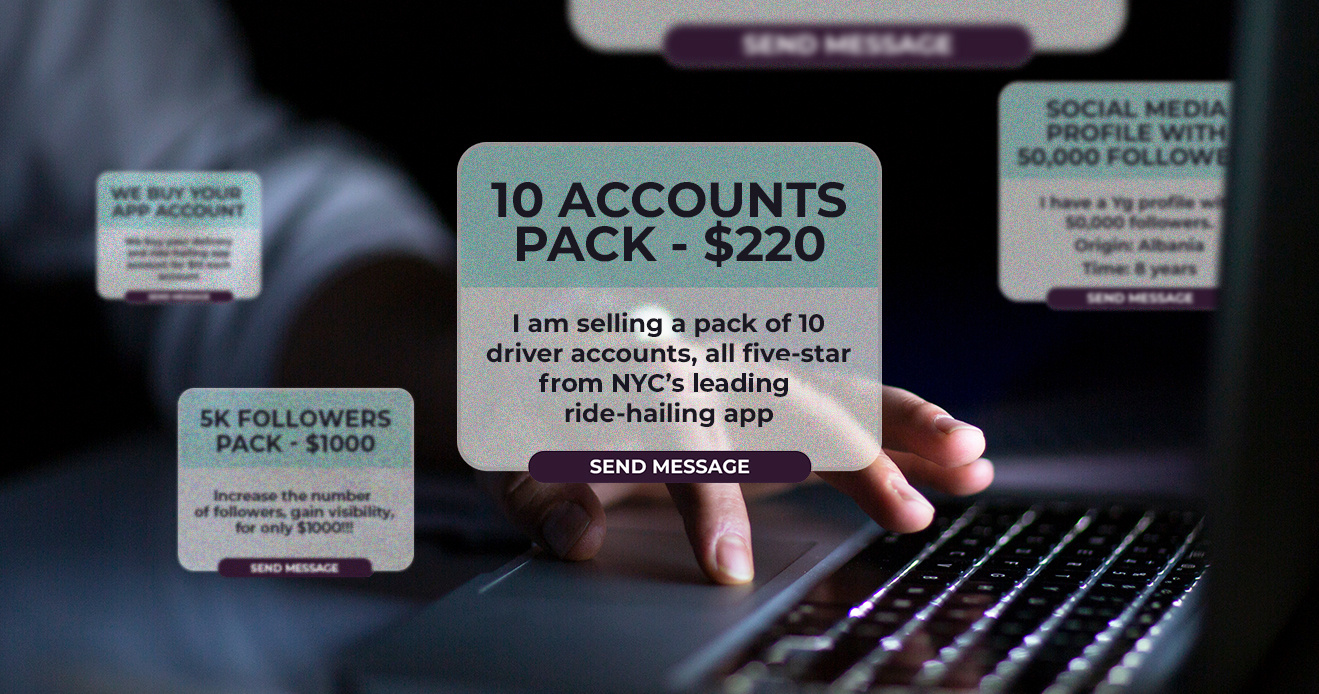
Fraud For Sale: Multi-accounting and Fraud on Gig Economy Apps
Take an insider look at the fraud-as-a-service tools used...

The Fraud-as-a-Service Economy: How Fraudsters Make a Living Attacking Gig Economy Platforms
Learn about the underground economy fueling fraud on gig...

The Fraudster's Playbook: How Fraudsters Defraud Your Platform
Learn about the step-by-step process fraudsters take to...

Device ID Obfuscation: How Fraudsters Make 1 Device Look Like 300
Learn about device ID obfuscation and how bad actors stop...

3 Fraud-as-a-Service Tools Every Food Delivery Platform Should Know About
Learn about the Fraud-as-a-Service tools impacting food...

You Are Who People Say You Are: Understanding the Reputational Impact of Courier Scams
Explore the real impact that courier scams can have on a...
Stopping Ban Evasion Even When Fraudsters Get Creative With Obfuscation
Prevent ban evasion by learning about fraudsters' tactics...

Why Browser Fingerprinting Has to Evolve to Support Financial Institutions & Online Marketplaces
Learn about threats facing online financial institutions...

The Ban Evasion Toolkit: Techniques Fraudsters Use to Evade Bans
Learn how fraudsters evade bans and discover effective...
Managing Friction and User Verification: Remembering the User’s Perspective
Explore how effective communication and user collaboration...

Smart Friction: Targeting Your Friction Toward Fraudsters, Not Good Users
Explore how smart friction and passive signals can enhance...
Playing the Numbers Game: Why Fraudsters Can Afford A 99% Failure Rate
Explore how multi-accounting enables fraud, and how...

The 4 Promotion Campaign Mistakes Fraudsters Feast On
Learn key mistakes to avoid in your promo campaigns to...

Balancing Growth Tactics With Fraud Prevention: How to Protect Promo Campaigns From Abuse
Learn key strategies to protect your promotional campaigns...
How Organized Fraudsters Run Their Operations Like a Business (And How Fraud Fighters Can Use That Against Them)
Explore how organized fraudsters exploit promotions and how...
Churn or Burn? Telling the Difference Between Low Retention and Promo Abuse
Learn how to tackle promo abuse with strategies on user...

Bad Actors at Scale: The Real Cost of Fraud & Policy Abuse
Explore how promo abuse at scale impacts businesses and the...
How Fraudsters Find Quick Workarounds For Fraud Prevention Tools (And How to Stay Ahead)
Learn how fraudsters outfox fraud prevention’s industry...
Communicating the Value of Fraud Prevention to Executives
Learn how to communicate the value of fraud prevention to...

Finding the Needle in the Haystack: Selecting a Vendor for Fraud Prevention
Discover industry expert insights about finding the right...

How to Overcome Fraudsters’ Speed Advantage and Stop Playing Catch Up
Discover how fraud prevention teams can overcome speed...
Data Quality: The Missing Piece of the Build vs. Buy Fraud Prevention Debate
Explore the build vs. buy dilemma in fraud prevention....

Taking a closer look at driver fraud response strategy on food delivery apps
Explore effective strategies to combat fraud on food...
Understanding 3 Different Types of Collusion on Food Delivery Platforms
Explore collusion on food delivery industry. Learn about...

Fraud on Restaurant Reservation Apps: How Bad Actors Are Ruining Dinner Plans & Stealing a Seat at the Table
Explore how bad actors are exploiting digital reservations,...

Having Your Delivery and Eating it Too: Managing Food Delivery Fraud Without Causing Driver Churn
Explore how food delivery platforms balance fraud...
The Hidden Costs of Internal Fraud Prevention
Should I invest in a third-party fraud prevention solution,...

The UV Balancing Act: Under-the-Radar Things to Consider When Balancing Fraud Prevention and User Experience
Learn keen insights related to balancing strong user...
3 Signs Your User Verification Friction is Too High
Explore signs that your user verification friction might be...
Unveiling the Hidden Threat: Tackling 'Off-line Rides' in Ride-Hailing Apps
Explore how offline rides impact ride-hailing platforms and...
Incognia: Strategic Expansion & Focus on Device and Location Data for Fraud Prevention
Learn about Incognia's $31M Series B funding round, our...

How & Why Driver Account Sharing Happens (And How Food Delivery Apps Can Prevent It)
Explore techniques to combat unauthorized account sharing...

Exploring 3 Different Location Spoofing Methods Used By Fraudsters
Dive into the 3 different location spoofing methods...

The Importance and Challenges of Listing Verification for Online Marketplaces
Explore how to enhance listing verification in P2P...
How Fraud Prevention and Marketing Can Work Together Against Promo Abuse
Explore how promo abuse impacts your digital marketing...

What’s Mine is Yours? How Ban Evasion and Account Sharing Are Costing Food Delivery Apps Money
Discover how food delivery platforms can combat fraudsters'...

Using Location Data to Detect Mule Accounts
Explore strategies to detect mule accounts in real-time...

Reduce fraud losses, increase profits: how fraud prevention functions as a profit center
Discover how fraud prevention makes important impact on the...
Optimizing Your Fraud Prevention Stack
Learn how to build the ideal fraud prevention stack, and...
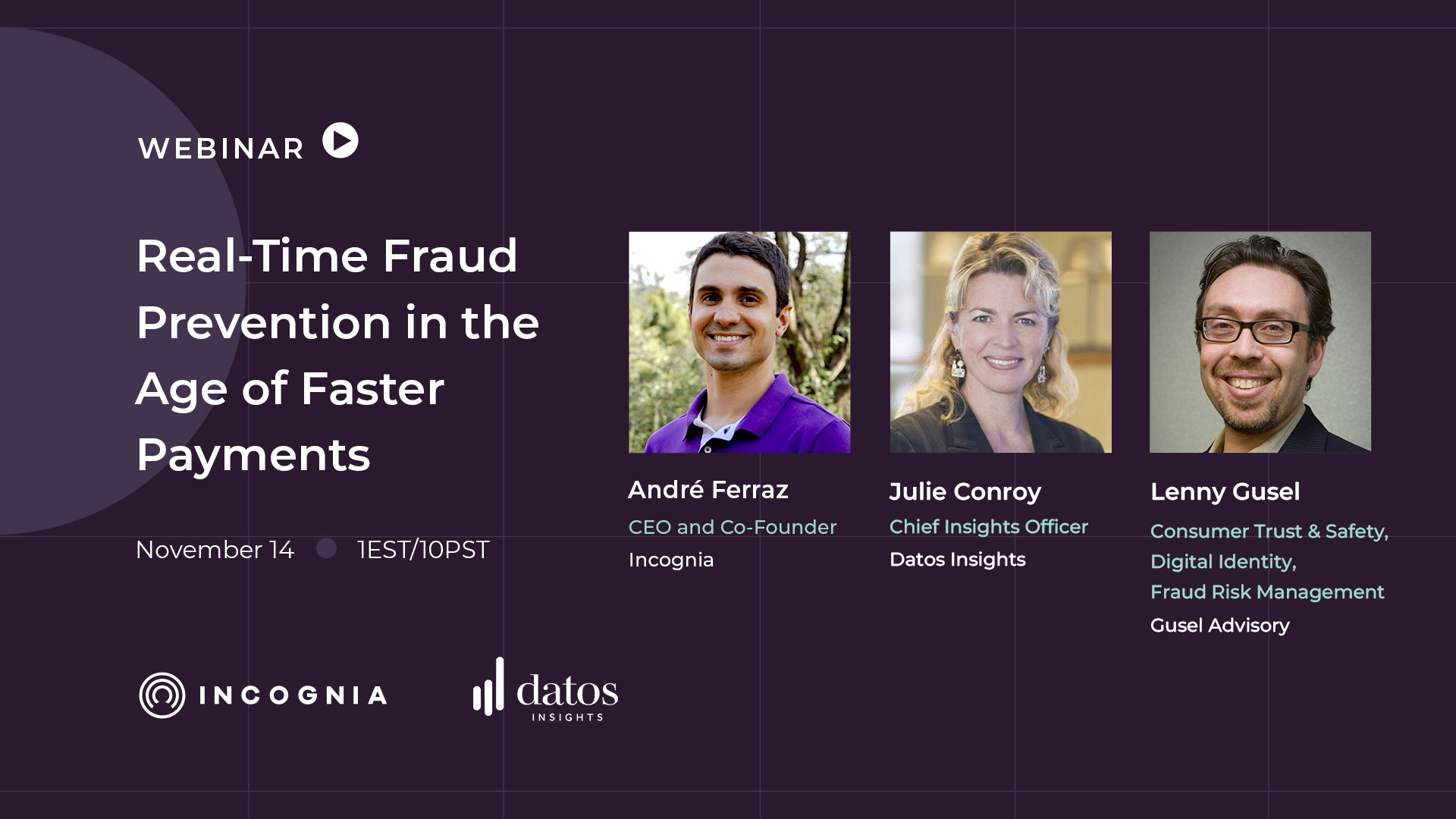
Real-Time Fraud Prevention in the Age of Faster Payments
Explore how real-time payment systems impact fraud...

Off-the-shelf device ID could be sabotaging your fraud prevention efforts
Explore the significance of device IDs in fraud prevention...

User Verification: The Importance of Achieving Real-time and Accurate Results
Dive deep into the core of user verification and learn how...
Marketplace Fraud: A Comprehensive Guide to Protect Your Platform and Customers
Explore how location intelligence can enhance fraud...
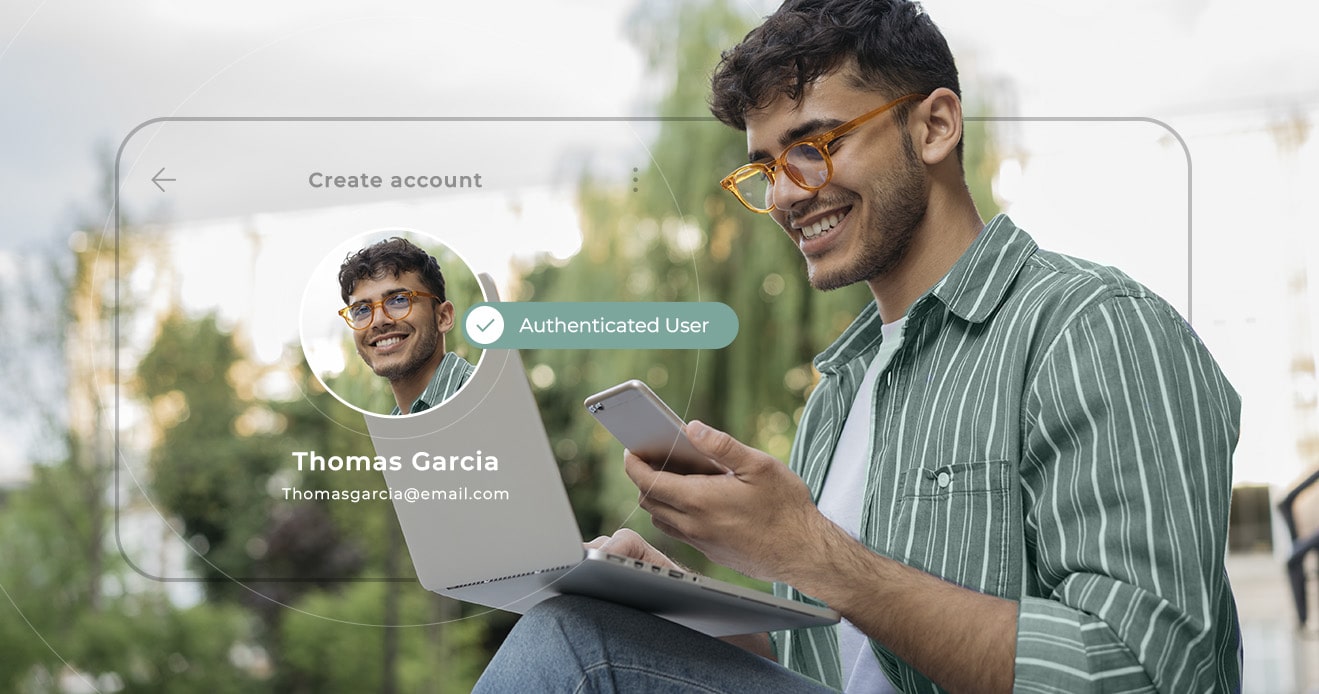
How to choose the best identity verification software
Explore identity verification software, how to choose the...

The Power of Location Verification: Strengthening Business Defenses Against Fraud
Discover how location verification safeguards businesses...

Incognia's advanced geolocation solution
Explore the evolution, benefits, and key aspects of...

Fighting ATOs with next generation device recognition
Explore insights from industry experts on the role of...

GPS verification: how is GPS used in security?
Discover how GPS verification enhances security and...

Fraud in Draw Games: How to Prevent iLottery Fraud
Explore the prevalent types of iLottery fraud, from payment...
![Featured image for Fraud prevention examples from along Incognia's journey [Podcast] resource](https://www.incognia.com/hubfs/Podcast_Peak%20ID.jpg)
Fraud prevention examples from along Incognia's journey [Podcast]
Dig into the recap of an interview with André Ferraz in...

The role of IP Address Verification in fraud prevention
Explore how IP address verification aids in fraud...

Identity verification is make-or-break for your platform's growth
Learn why identity is the cornerstone for trust & safety on...

Gambling Compliance: How to Add Extra Layer of Protection
Discover how multiple layers of security can ensure safer...

Device authentication for fighting fraud: when your phone is your new password
Learn about device authentication as a security measure,...

Detecting suspicious environments is a paradigm shift
Discover how detecting suspicious environments reveals new...
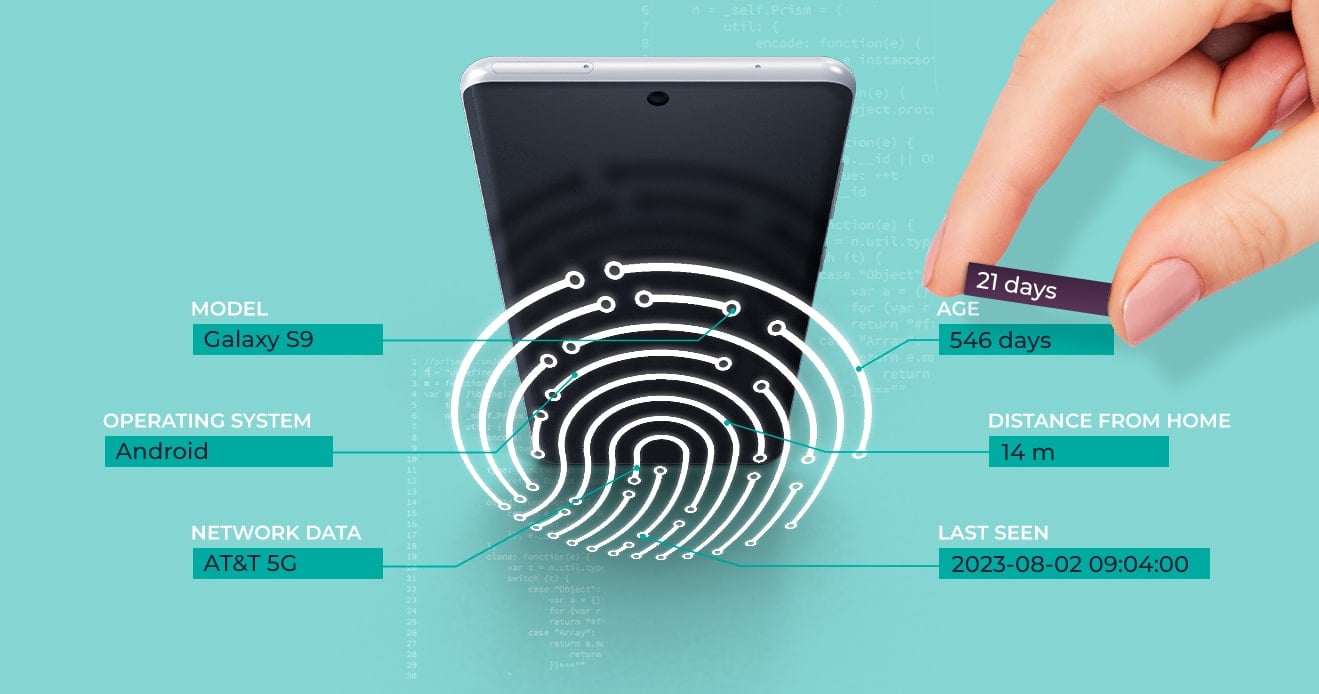
A Comprehensive Analysis of Device Fingerprint Spoofing Techniques
Read to understand the evolution of device fingerprinting...
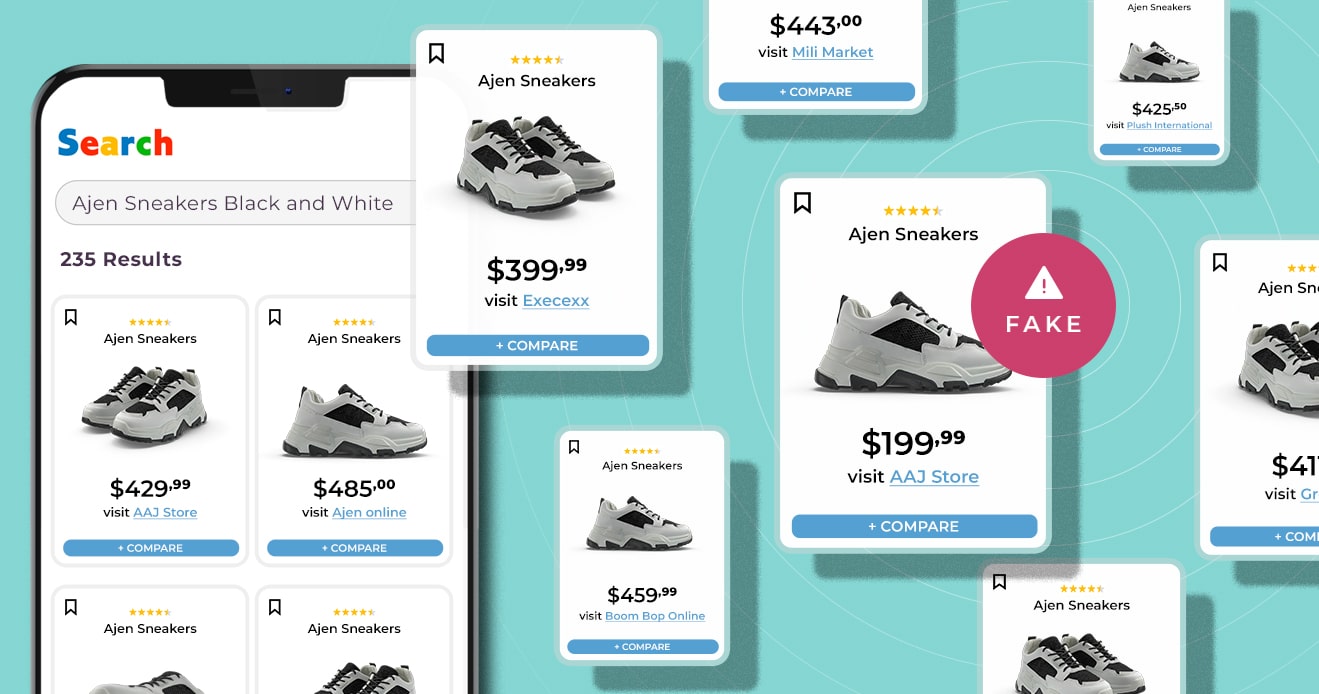
The Current State of Fraud Prevention and Detection
Protect your business from fraud with effective prevention...

Cutting Through the Noise: 2 generative AI threats to prepare for
Discover the two generative AI threats that fraud...
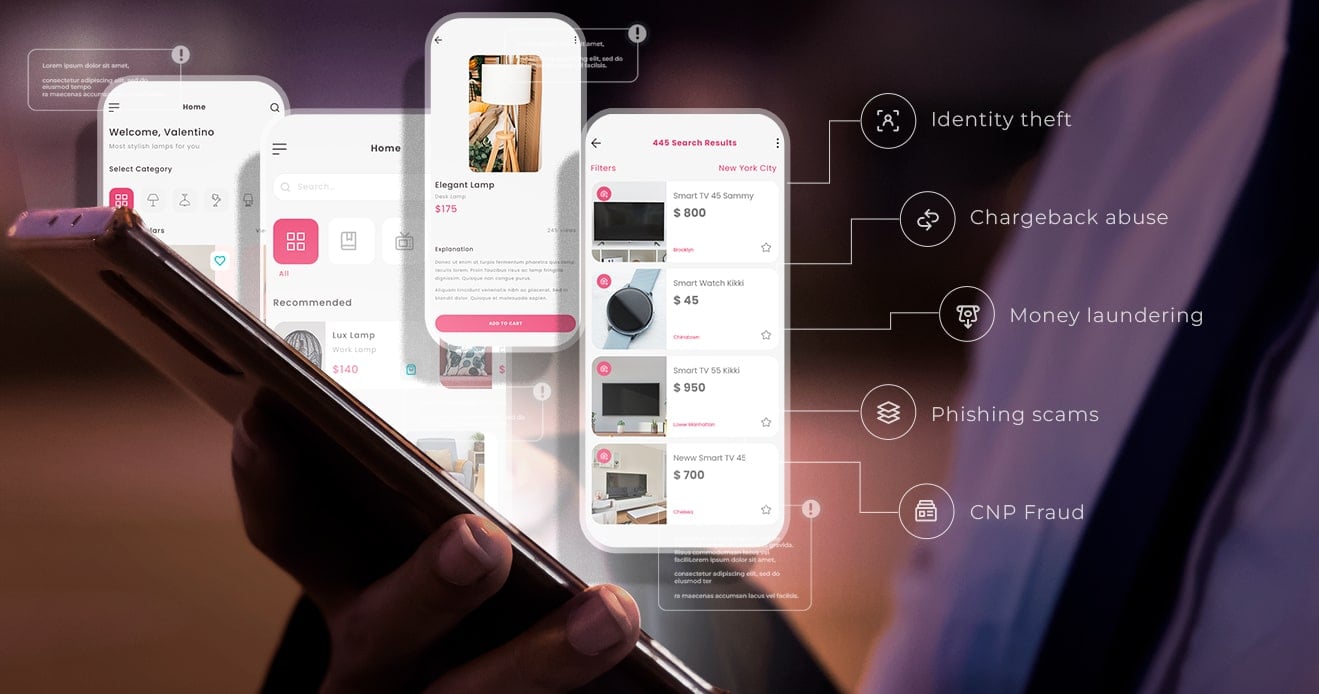
4 strategies for mitigating fraud risks on your P2P marketplace
Discover four robust strategies to mitigate fraud risks on...
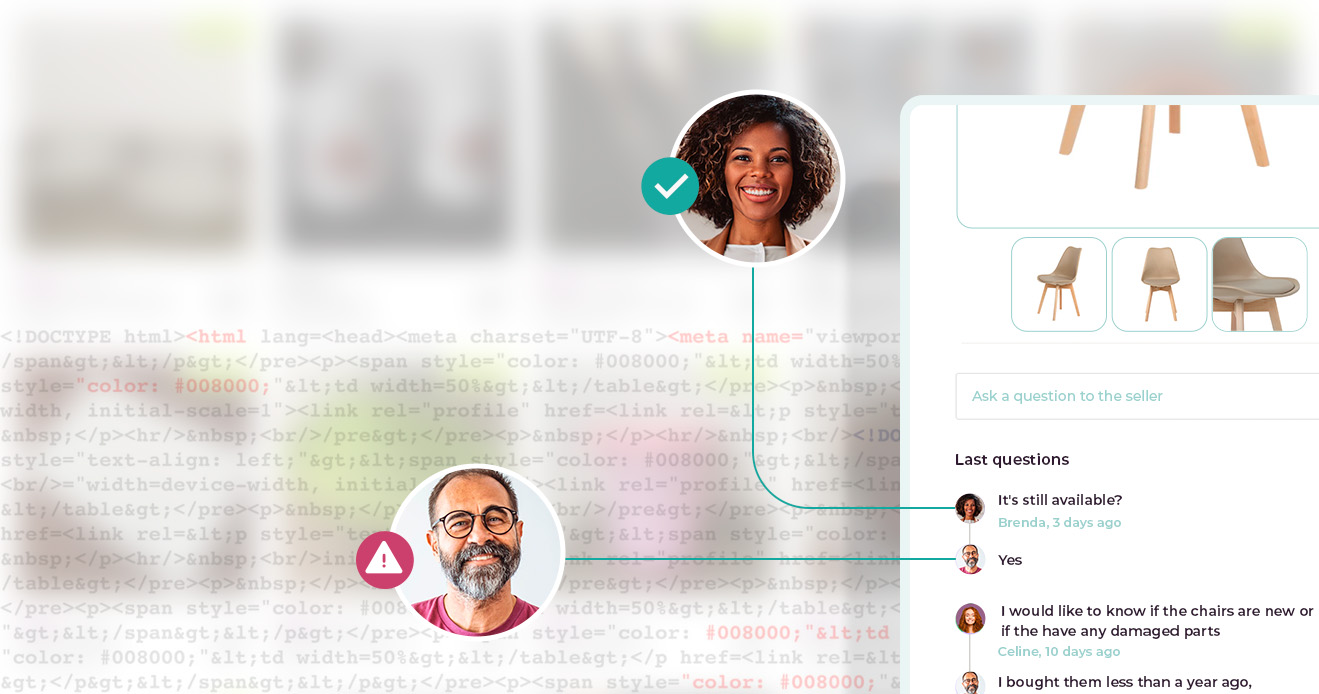
Using Seller Fraud Detection to Prevent Marketplace Scams
Discover how to detect risk signals and prevent potential...

Gaming fraud: How fraudsters stack the deck against iGaming operators (and what can be done about it)
Learn about different types of gaming fraud and how a...

Location Fingerprinting: A new era in fraud prevention
Learn how cutting-edge location fingerprinting technology...

5 Best Practices for Preventing Refund Fraud in Food Delivery
Safeguard the integrity of your food delivery service!...

Ban Evasion: How can it be detected and prevented?
Struggling with ban evasion on your platform? Learn how you...

Key takeaways from the 2023 Marketplace Risk Management Conference
Discover key takeaways from the 2023 Marketplace Risk...

Main policy violations & scams in food delivery apps
Are you a food or grocery delivery app? Find out what...
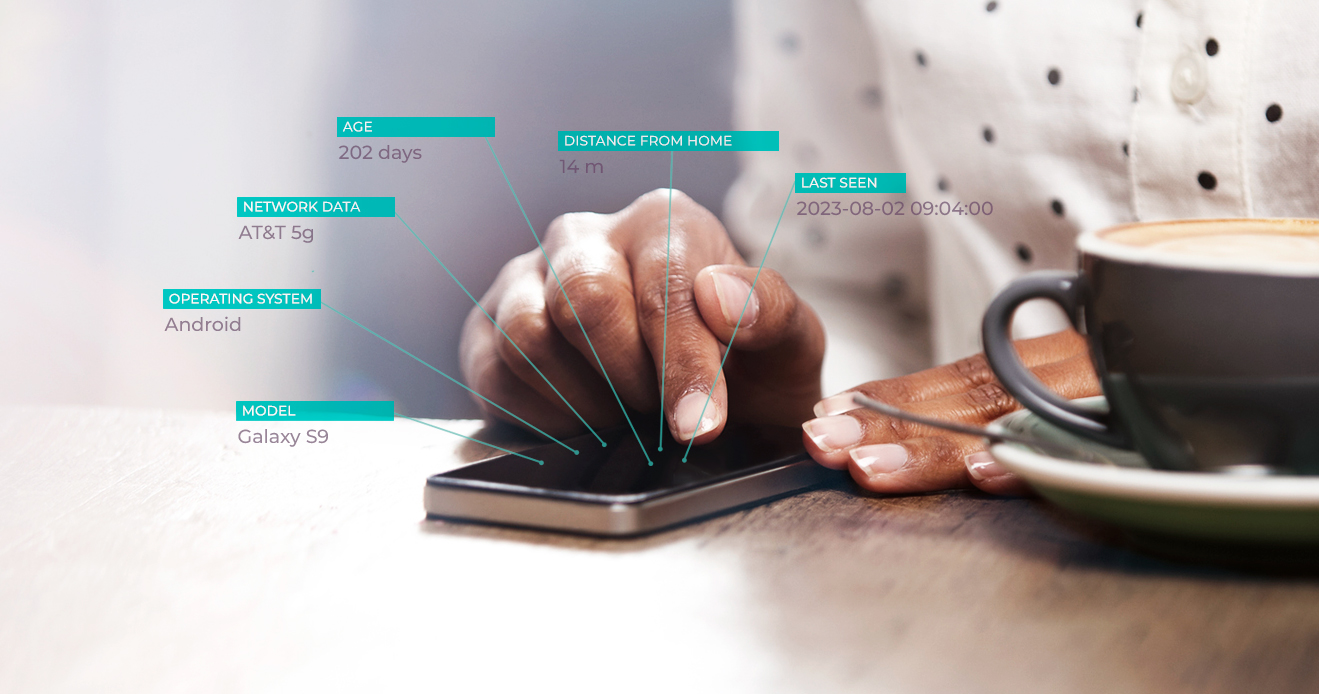
The next generation of device fingerprinting
Get ahead of fraudsters with Location Fingerprint. This...

As device fingerprinting becomes more challenging new risk signals emerge
Bringing new behavioral signals to the market, and...
GPS tracking for delivery drivers is only as effective as its tamper-resistance technology
Maximize GPS tracking for delivery drivers with...
![Featured image for How to Reduce Bonus and Promo Code Abuse in Food Delivery [Guide] resource](https://www.incognia.com/hubfs/promo-code-abuse-in-food-devivery.jpg)
How to Reduce Bonus and Promo Code Abuse in Food Delivery [Guide]
Prevent promo code abuse in food delivery apps: Learn about...
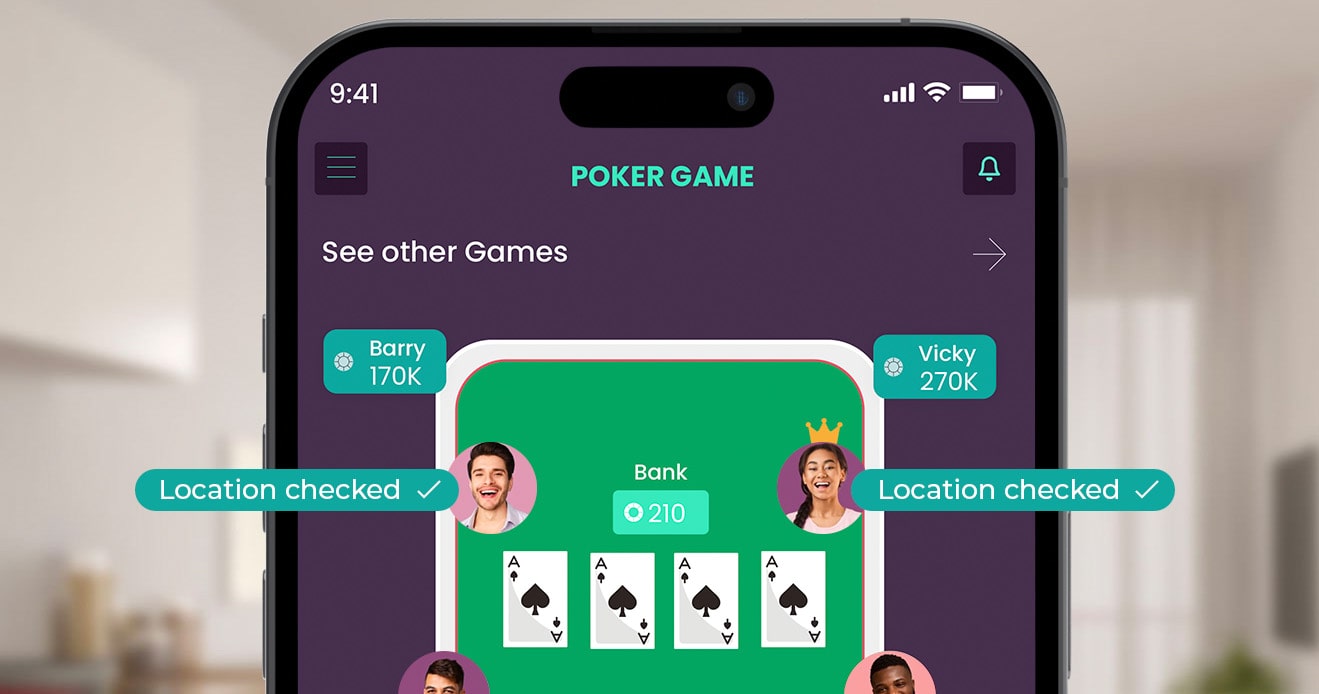
Player Location Check
Read this blog now and learn about challenges and solutions...

The Shared Account Challenge: Best Practices for Securing Food Delivery Apps
Are you a food delivery app struggling to prevent...

Courier Scams: How Location Verification Can Uncover Them
Find out what scams couriers commit and how location...
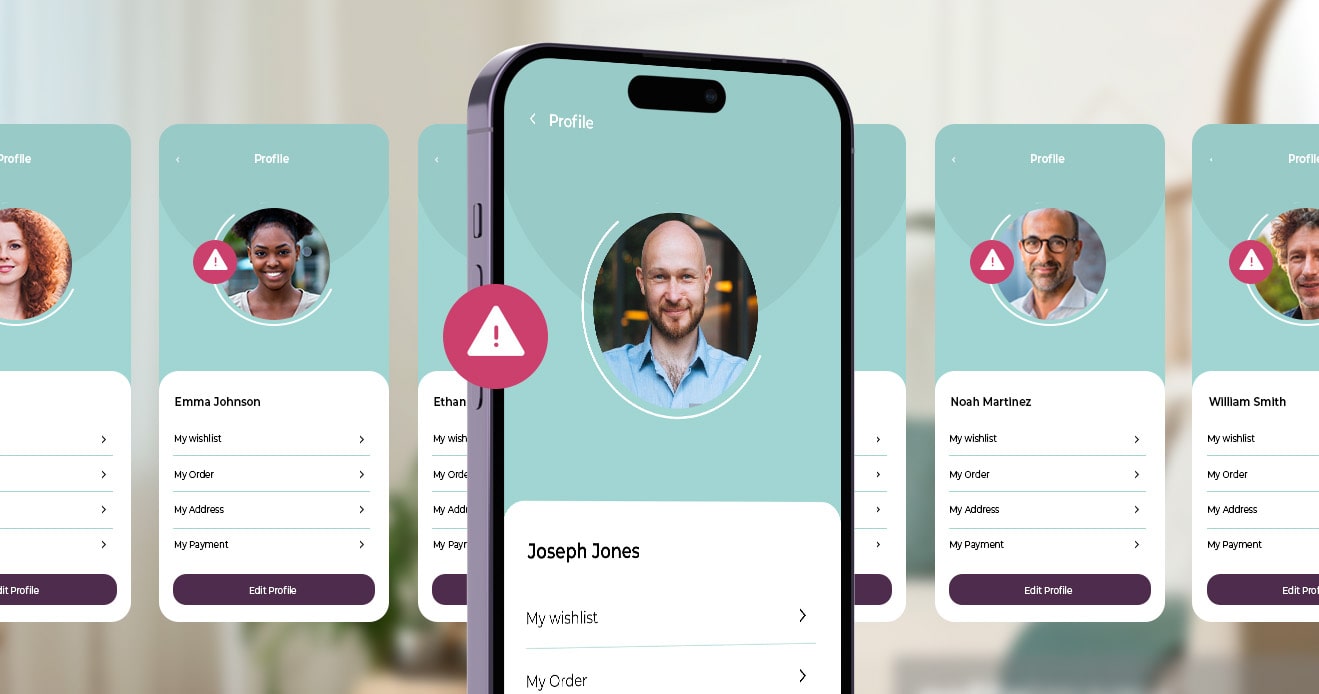
Account creation fraud: How to detect multiple accounts in food delivery apps?
Protect your app's integrity and avoid revenue losses with...
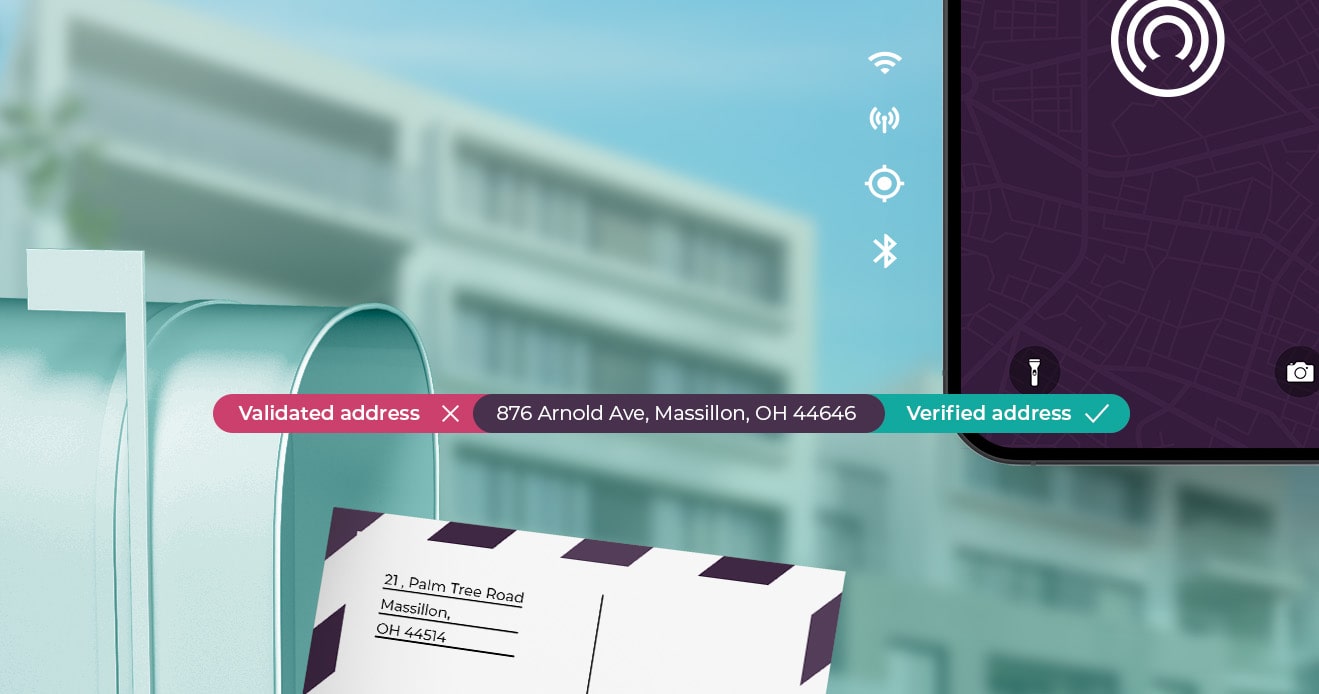
When to Use Address Verification Instead of Address Validation Software
Get up to speed on the difference between address...
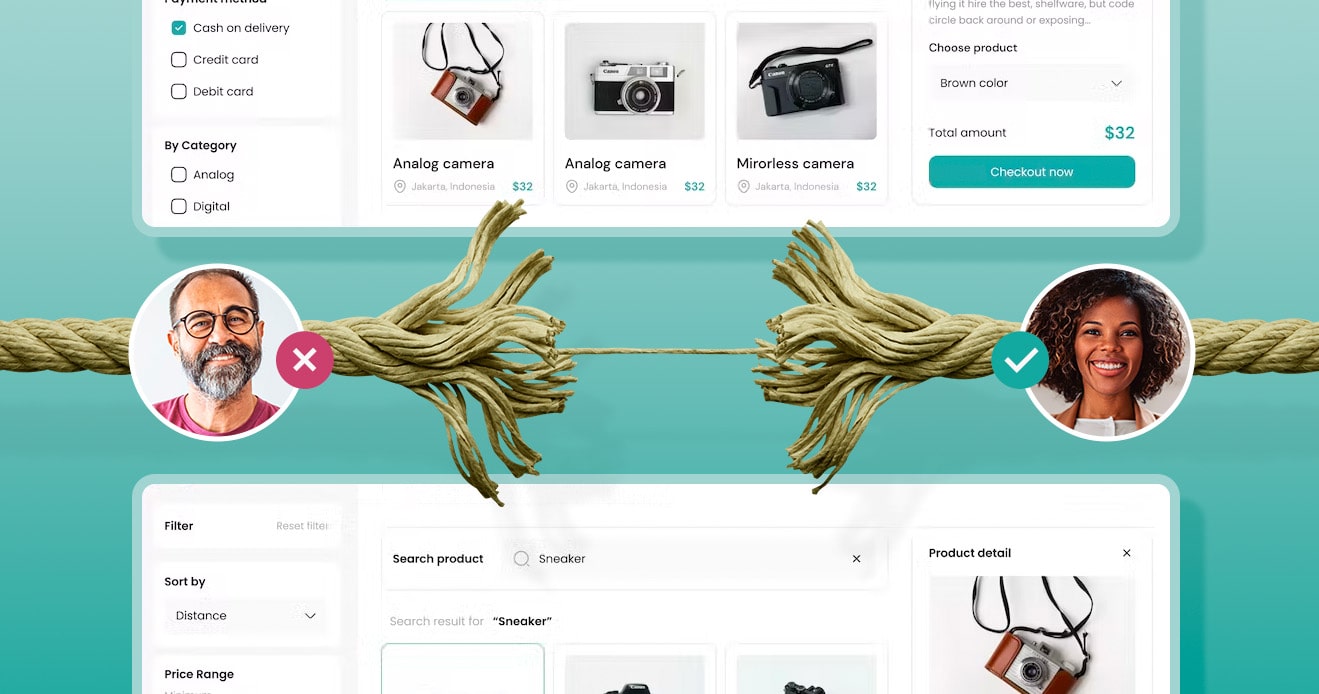
Why Online Identity Verification is Critical for Peer-to-Peer Marketplaces
Find out why online identity verification should be an...

The State of User Verification for Peer-to-peer Marketplaces
For online marketplaces, efficient user verification...

Machine Learning: How Incognia Data Makes the Difference
In this article, we take a closer look at how Machine...

How Real-Time Address Verification Can Improve User Acquisition
Learn how Real-Time Address Verification can help save...

A Better Way To Do International Address Verification
Discover the challenges of international address...

The Fundamentals of Real-Time Address Verification
In this article, we take a closer look at the fundamentals...
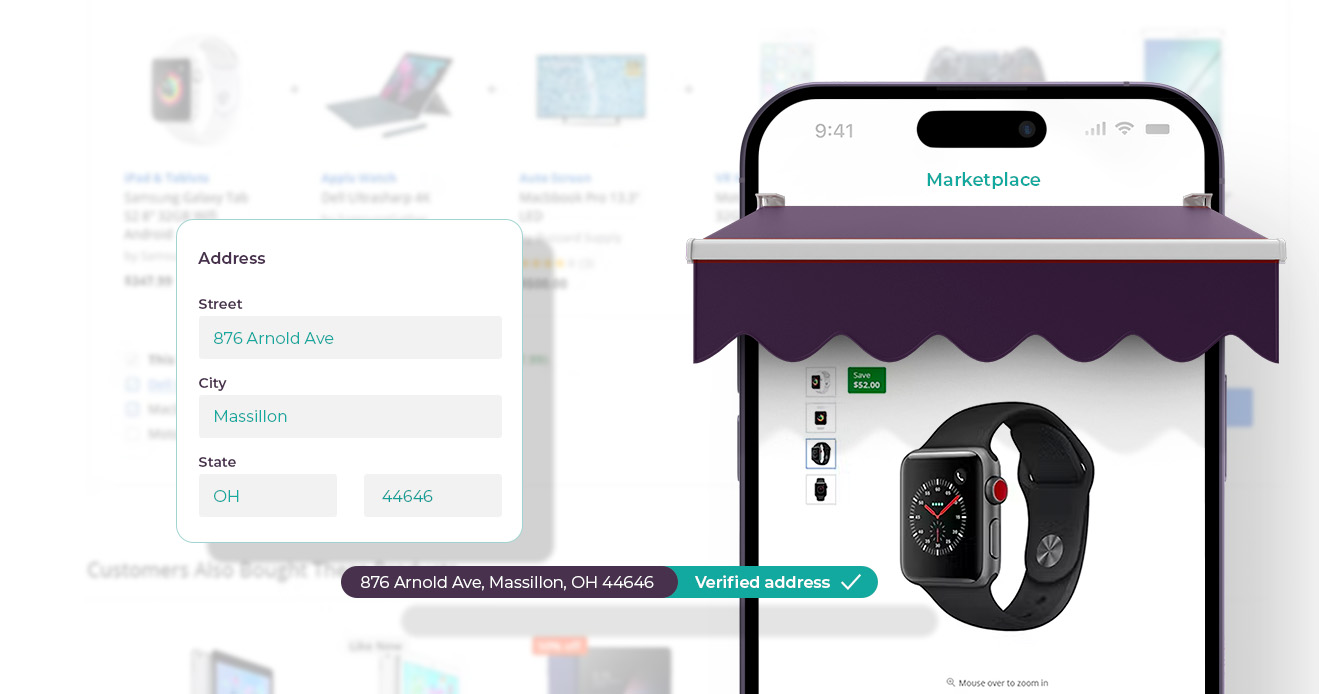
5 Challenges Address Validators Solve for P2P Marketplaces
Address validators can help P2P marketplaces improve the...
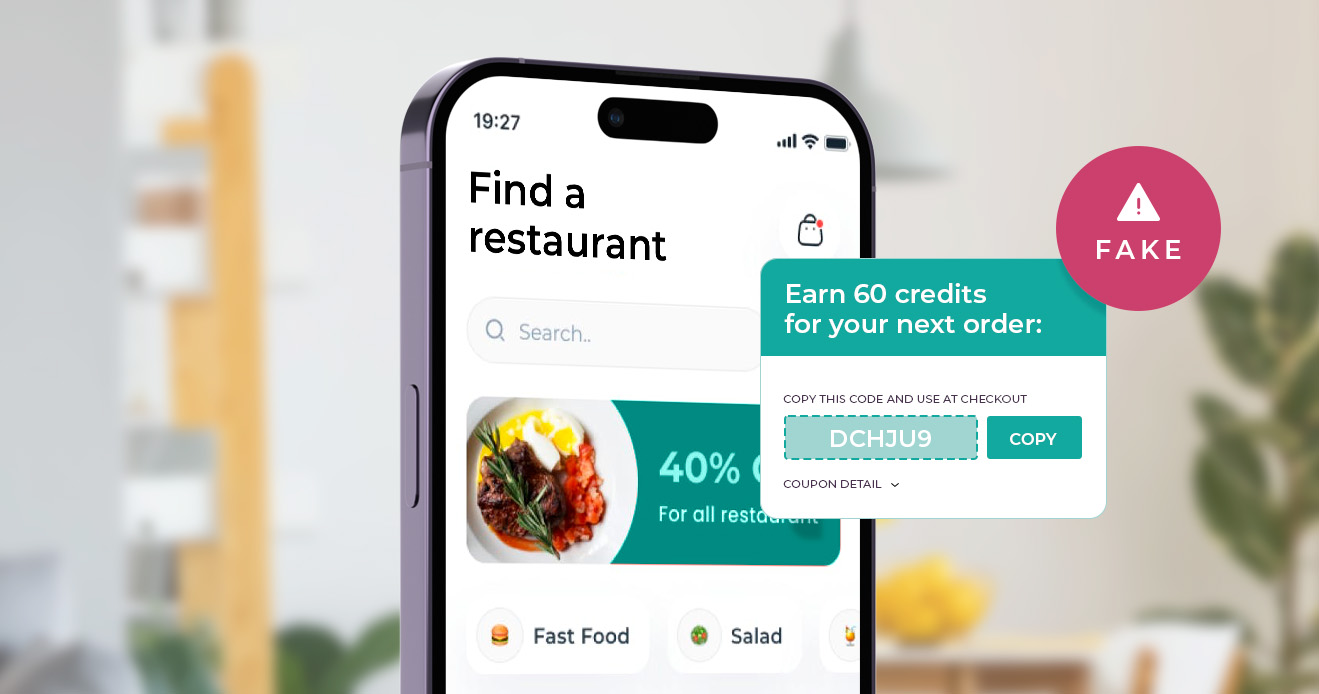
How Delivery Platforms Can Detect Coupon Scams
Learn how to detect promotion and coupon scams to protect...

Top 5 Most Common Address Verification Software
Find out which five types of address verification software...
Privacy and Data Protection: 3 global trends for 2023
Find out what are some of the global trends in the privacy...

How to detect and block the location of Fraudsters and Bad Actors
Understand why you should leverage Incognia’s new...

What will the digital identity space look like in 2023?
Find out what the predictions are for digital identity in...

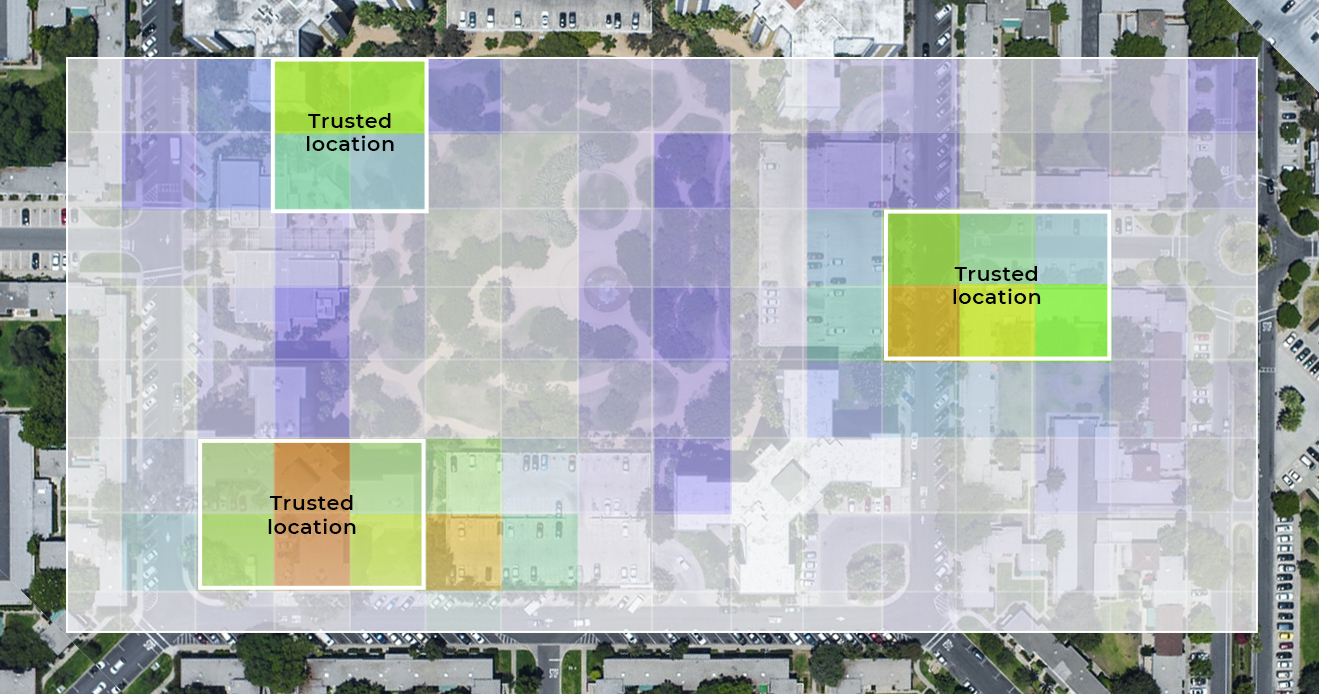
How long does it take to establish a user’s 'Trusted Location'?
Understand how long does it take to Incognia establish a...

The Pragmatist’s Approach to the Application of Facial Recognition
Biometric authentication has benefits and drawbacks. A...

The Science Behind Incognia's Location Identity
From academic research to a powerful digital identity...

Scams pose a threat to the gig economy apps
Fraud and policy abuse on gig economy apps hurt the user...

Who is faking location?
Location spoofing poses a threat to apps that rely on...
How Location Technology Can Make Trust & Safety More Cost Effective
Building a trust and safety team is expensive, and...
Fraud farms - Identifying where fraudsters are
Fraud farms are massive operations wherein fraudsters use...

Incognia is featured in the best authentication solutions on Cybernews
The experts from Cybernews recently took notice of our...

Recognizing and Solving Trust & Safety Challenges for Food Delivery
What are the main Trust & Safety challenges for Food...

5 Industries Location Identity Can Help Increase Trust & Safety
Location identity is a powerful tool for fraud detection...

Fraudsters Use Location Spoofing to Take a Bite from Food Delivery Apps
Fraudsters Use Location Spoofing to Take a Bite from Food...
Spoofing-resistant location data - the missing piece to addressing digital trust and safety
Location data is essential for digital trust and safety,...

The Rise of the Super App and the Role of Location
In location-based apps, such as food delivery, all users...
![Featured image for Geolocation [An updated definition for identity, authentication, and fraud prevention] resource](https://www.incognia.com/hubfs/Geolocation%20-%20An%20updated%20definition%20for%20identity%2c%20authentication%2c%20and%20fraud%20prevention_.jpg)
Geolocation [An updated definition for identity, authentication, and fraud prevention]
The definition of what geolocation is, and what it can do...

Swipe Left for Location Spoofing
Study of 24 leading dating Apps shows 37% can be location...

A Review of the New Federal American Privacy Bill
New Federal American Privacy Bill - This bill represents...

Incognia appoints new DPO and reinforces its commitment to privacy
New DPO reinforces Incognia's values and mission related to...

Incognia introduces new Location-based Liveness Spoofing Detection Solution
Today we announced a new Incognia identity fraud detection...

How to Achieve High Opt-in Rate When Requesting User Location Permissions
Learn how to boost opt-in rates for user location...
Incognia Closes $15.5M Series A Funding Round
Incognia announces the closing of our $15.5M Series A...

How to block users playing outside of licensed jurisdictions
Online gambling is regulated, limiting individuals to...

Fraud farms take advantage of location spoofing to swindle mobile gaming apps
With fraud farms, fraudsters are able to mechanize and...
Apple announces use of location for fraud prevention
Apple Pay is now using location for fraud prevention. This...

Incognia introduces Location-based Device Authorization Solution
Incognia announces a new identity fraud detection module to...

Cybernews Interview with André Ferraz
Cybernews interview with André Ferraz on the need for...
Why is device fingerprinting useless when fintech apps need it most?
Device fingerprinting will not recognize the login of a new...

Authentication Mobile App Friction Report - Crypto Edition
A review of authentication friction in top crypto apps at...
Incognia Introduces New Location Identity Fraud Detection Tools
Incognia announces new location identity fraud detection...
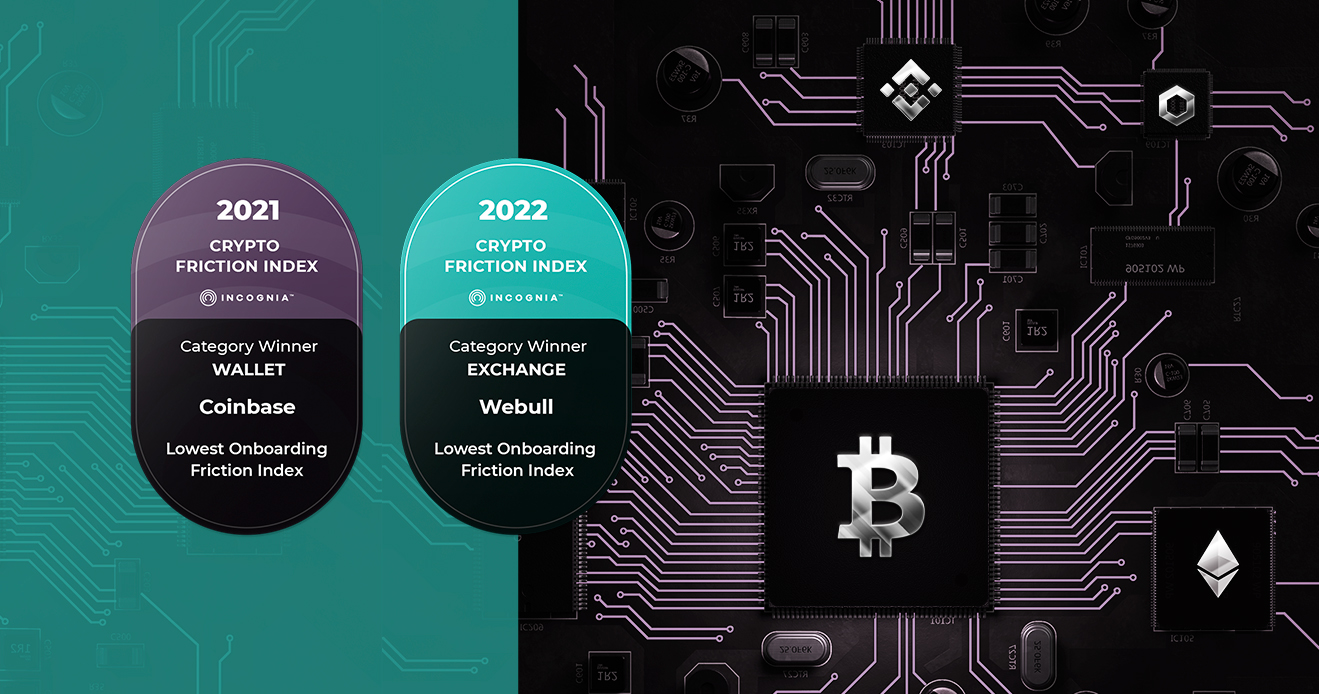
New Crypto Edition of Mobile App Friction Report
Incognia releases Crypto edition of Mobile App Friction...
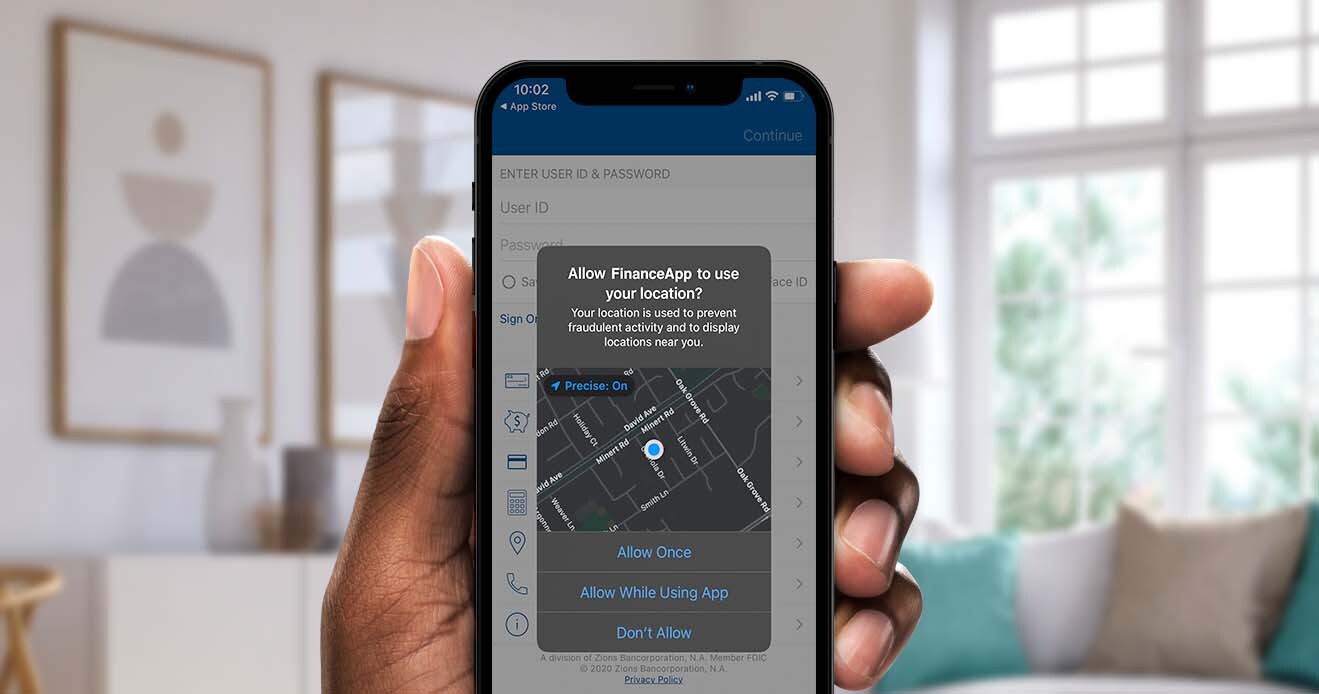
Thoughts about location data privacy and consent
Lucas Martins, Incognia CSO, shares insights and...
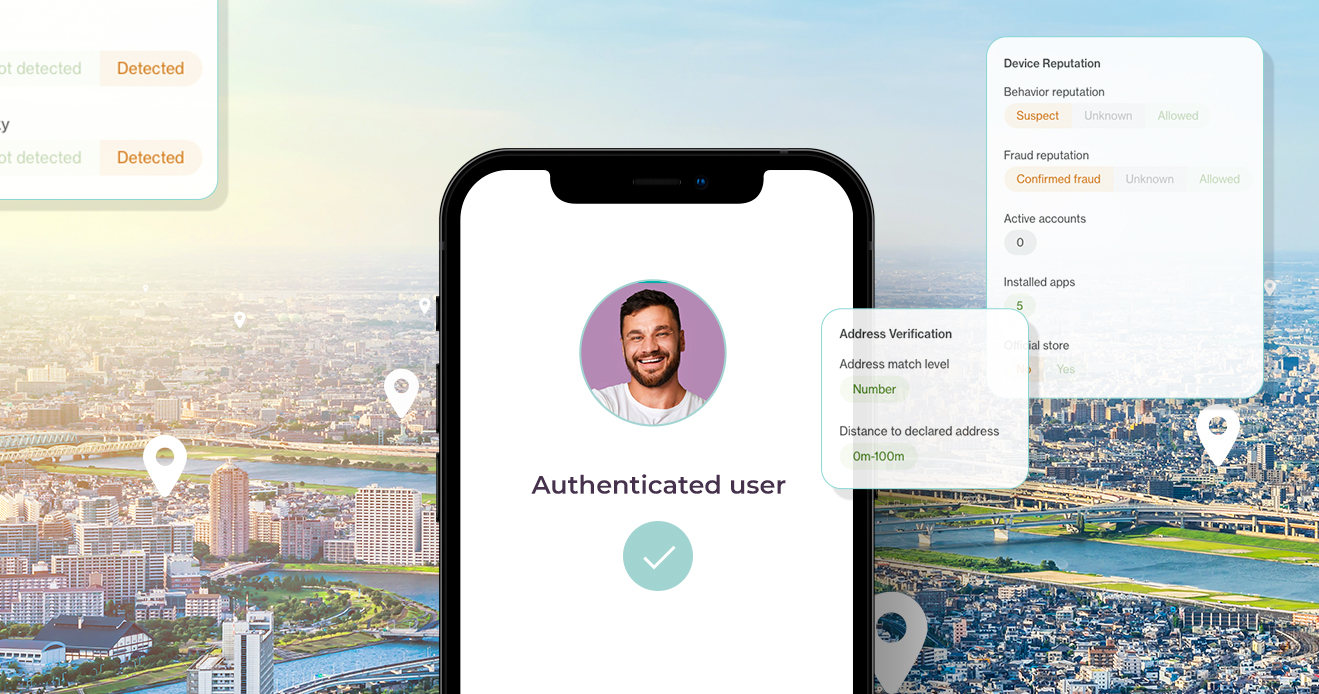
What lies beneath a highly precise fraud risk assessment?
Learn how location behavior and device intelligence power...
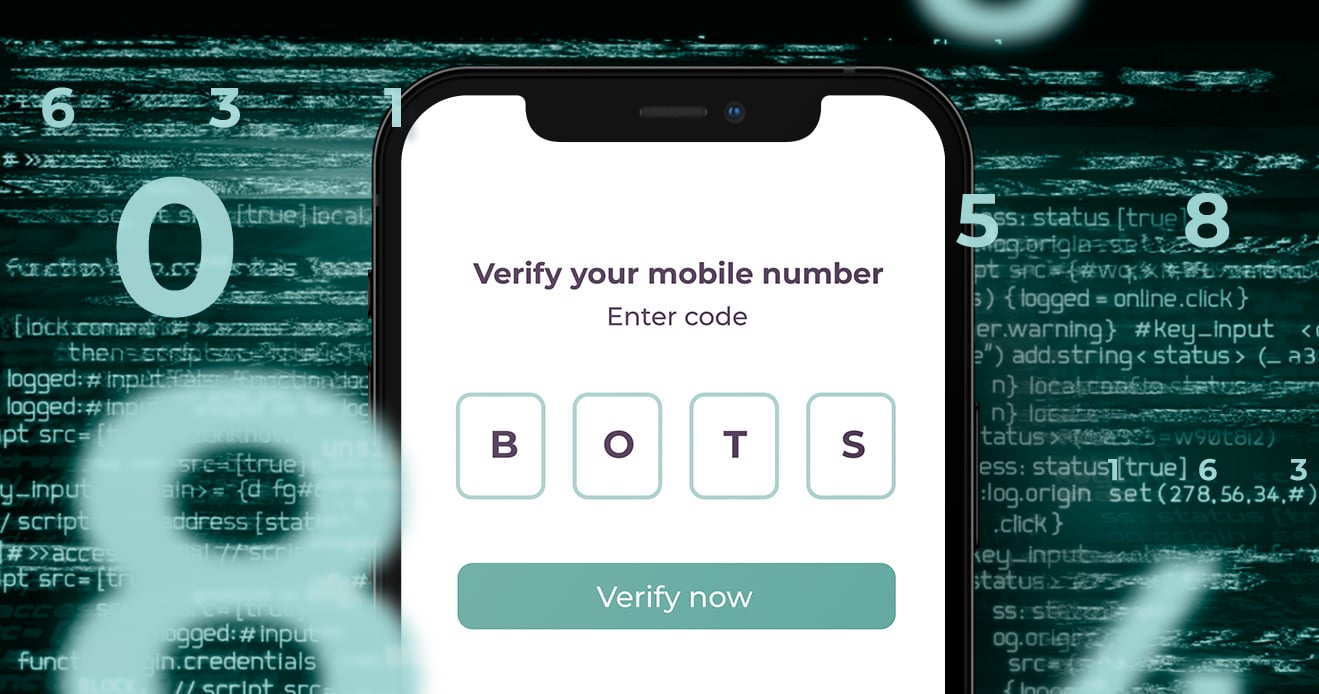
Could OTP security get any worse? Yes. Bots.
Bots are being used to automate the theft of one time...

Why Incognia when considering behavioral biometrics
Location behavior offers a compelling authentication signal...
Why it's time to stop relying on static credentials
Static credentials are vulnerable to exposure via social...

Why OTPs shouldn't be part of a passwordless strategy
A one time password (OTP) is a password that lasts for just...

It's time to stop blaming the user
Social engineering is becoming increasingly sophisticated...
![Featured image for Fintech Mobile App Friction Ranking [Device Change] resource](https://www.incognia.com/hubfs/App%20friction%20device%20change.jpg)
Fintech Mobile App Friction Ranking [Device Change]
Incognia Mobile App Friction report ranks Klover and...

Buying a new smartphone is not a crime
From time to time people switch devices, but this doesn't...
![Featured image for Food Delivery Apps [Detecting Location Spoofing Fraud] resource](https://www.incognia.com/hubfs/food%20delivery%20apps_3.jpg)
Food Delivery Apps [Detecting Location Spoofing Fraud]
Food delivery apps are now wildly popular and new fraud...

What is zero-factor authentication?
Companies are looking to adopt passwordless authentication....
![Featured image for Fintech Mobile App Friction Ranking [Login Authentication] resource](https://www.incognia.com/hubfs/featured-image-blog-mobile-app-friction-report-v2.jpg)
Fintech Mobile App Friction Ranking [Login Authentication]
Incognia Mobile App Study ranks Klover and eToro winners...

Mobile Authentication - Security and Friction Rankings
Learn how the different types of mobile authentication rank...
The secret of increasing the opt-in rate on your mobile application
Learn 5 things to know about Location Permissions, an ebook...

Solving the digital identity problem for mobile and beyond
Digital identity is a challenging problem and far from...

Why Location is Hard to Get Right
Applying location technology to mobile fraud prevention is...

Why Precise Location Matters for Mobile Fraud Prevention
With 50% of transactions happening on mobile devices, and...

Five Ways Fraudsters Spoof Location
Location spoofing is now a standard technique used by...

How should location fit into a risk based authentication strategy?
How to implement frictionless risk based authentication...
Account Takeover Prevention Using Location Behavior
Strong Account Takeover Prevention could be achieved...

Incognia: A Great Place to Work
Incognia was recently certified as a great place to work by...

Real-time address verification for mobile
With increasing mobile adoption, use of real-time address...

Global QSR Approves More Mobile Transactions with Incognia
Incognia dramatically increases approval rates for mobile...

Incognia Wins 2021 DEVIES Fintech Award
The Incognia Mobile Antifraud SDK was chosen as the best...
![Featured image for Fintech Mobile App Ranking [Onboarding Friction Index] resource](https://www.incognia.com/hubfs/%5BFEATURED%5DApp%20friction%20report.jpg)
Fintech Mobile App Ranking [Onboarding Friction Index]
Incognia Mobile App Study ranks Chime, Robinhood and Credit...
![Featured image for Hide and Seek [Mobile Emulators and Location Spoofing] resource](https://www.incognia.com/hubfs/%5BFEATURED%5DHide%20and%20Seek%20%5BMobile%20Emulators%20and%20Location%20Spoofing%5D.jpg)
Hide and Seek [Mobile Emulators and Location Spoofing]
Detection of mobile emulators and location spoofing for...
![Featured image for [2020 Hot Trend] QR Code Contactless Payments resource](https://www.incognia.com/hubfs/%5BFEATURED%5D%20Finally%20a%20%28Real%29%20Use%20for%20QR%20Codes%20%281%29.jpg)
[2020 Hot Trend] QR Code Contactless Payments
Finally the QR Code has found its real purpose -...

Frictionless Fraud Detection Meets Contactless Payments
Contactless payments usage surges due to health concerns....
Social engineering prevention with dynamic data
Implement dynamic data into your risk decisioning to...

Removing the Friction & Fraud from Mobile Financial Services
Growing business means growing mobile accounts - learn how...
![Featured image for How much Friction is too much Friction? [Balancing UX and Security] resource](https://www.incognia.com/hubfs/%5BFEATURED%5DHow%20much%20friction%20is%20too%20much%20on%20UX_.jpg)
How much Friction is too much Friction? [Balancing UX and Security]
Users are reaching the limits of how much friction they...

Facial Recognition: What can possibly go wrong?
Facial recognition technology is being questioned,...

The True Cost of False Positives in The Battle to Prevent Fraud
False positives are also a challenge in fraud prevention,...
![Featured image for Prevent Mobile App Fraud [The Most Expensive Form of Identity Theft] resource](https://www.incognia.com/hubfs/%5BFEATURED%5DPreventing%20Mobile%20Application%20Fraud%20%5BThe%20Most%20Expensive%20Form%20of%20Identity%20Theft%5D.jpg)
Prevent Mobile App Fraud [The Most Expensive Form of Identity Theft]
Application fraud is a billion dollar problem for financial...
![Featured image for Fraud During the Pandemic [5 Key Trends] resource](https://www.incognia.com/hubfs/%5BFEATURED%5DFraud%20in%20the%20time%20of%20covid-19.jpg)
Fraud During the Pandemic [5 Key Trends]
COVID-19 has quickly changed consumer behavior allowing new...
![Featured image for Synthetic Identity Fraud [What You Need to Know] resource](https://www.incognia.com/hubfs/%5BFEATURED%5D%20Synthetic%20Identity%20Fraud%20%5BEverything%20You%20Need%20to%20Know%5D.jpg)
Synthetic Identity Fraud [What You Need to Know]
Synthetic identity fraud is fueled by data breaches and...

We Are Incognia
At Incognia we have created a private identity based on the...
![Featured image for Protecting Location Data [5 Core Pillars] resource](https://www.incognia.com/hubfs/US/blog/%5BFeatured%20Image%5D%20Protecting%20Location%20Data%20%5B5%20Core%20Pillars%5D.jpg)
Protecting Location Data [5 Core Pillars]
Collecting, storing and working with location data raises...
![Featured image for Location Behavioral Biometrics [A New Type of Digital Identity] resource](https://www.incognia.com/hubfs/US/blog/%5BFEATURED%20IMAGE%5D%20What%20is%20location%20behavioral%20biometrics.jpg)
Location Behavioral Biometrics [A New Type of Digital Identity]
Location-based behavioral biometrics offers the opportunity...

